Why choose behavior-based DLP?
The behaviors leading up to a data exfiltration event are more important in differentiating the types of insider risk and determining next steps than the event itself.
Better DLP in an integrated platform


DTEX InTERCEPT BEHAVIORAL DLP
Take a next-level approach to identifying and mitigating data loss events, with near-zero performance impact to endpoints or the network.
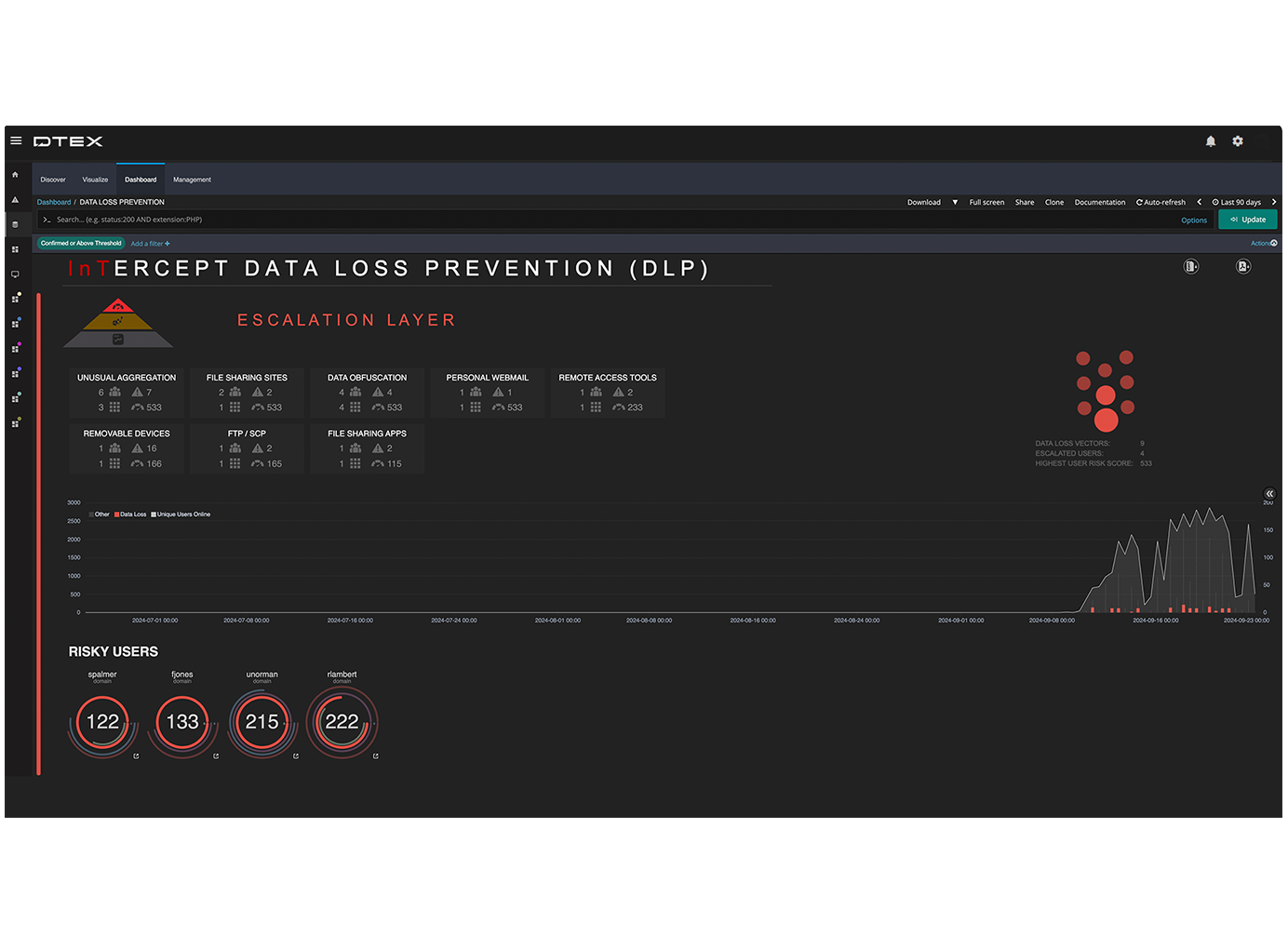
Stop data loss with behavioral intelligence.
Gain insight into file changes with activity-based context.
Enrich data protection with insider risk scores.
Accelerate incident response with real-time digital forensics.
The behaviors leading up to a data exfiltration event are more important in differentiating the types of insider risk and determining next steps than the event itself.

Behavior-based
Correlate behavioral context with data changes for a better understanding of intent.
File Lineage
Track file history – in use, in motion, and at rest, on and off network – to understand usage and modifications.
Inferred Sensitivity
Identify sensitive information through classification labels and content creator behavior.
One-click Reporting
Summarize data handling trends for fast, real-time information sharing & response escalation.
Amplify your insider risk posture through our partnerships and powerful integrations. DTEX seamlessly connects with your existing security ecosystem to deliver holistic threat protection.












































Superb product, and even identified a data exfiltration event during the demo. The product is superb, and the experience with the sales and technical teams has been great.”
CFO, Healthcare and Biotech

Prior to DTEX, we were reactionary. Instead of preventing instances, we were recovering from them, so the potential for loss of data was much higher. The potential that we wouldn’t be able to identify and correlate an event that happened six months ago to an event that happened today changed the potential severity of the escalation.”
Director of Insider Risk, Pharmaceuticals

We’ve been able to identify exfiltration activities with DTEX and have had incidents related to that. Some of these have been the underlying cause due to a failure on an internal control, while others were a result of another part of the technology stack that should be stopping it but didn’t. DTEX was able to then detect the activity.”
Manager, Global Cyber Defense Intelligence, Technology