Uncovering foreign interference:A DTEX case study
AI R&D proves high risk for IP theft
DTEX successfully intercepted a foreign national who had been planted to steal AI research from a global tech firm. InTERCEPT™’s underlying dataset and forensic audit trail were ultimately used to support prosecution. Watch the video to see how the investigation played out.
DETECT
Be aware
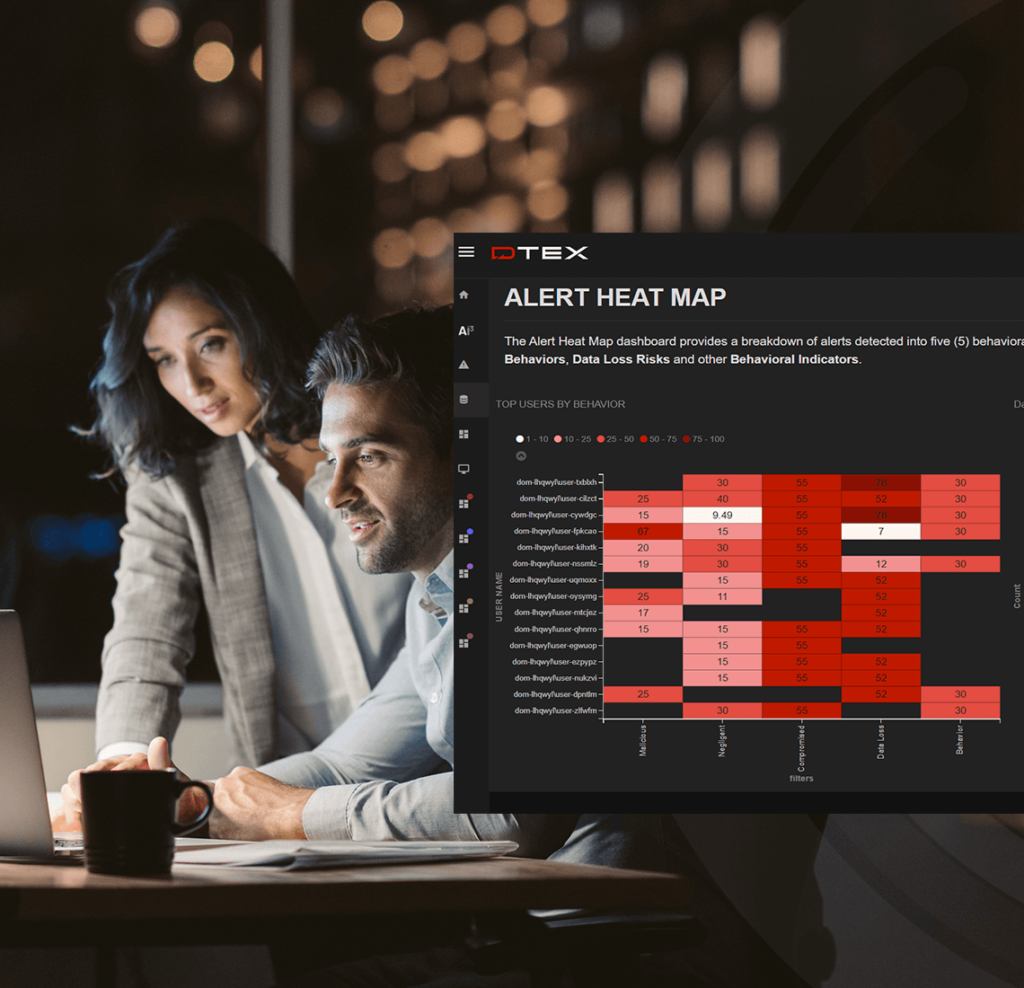
Don’t be caught blindsided. Get the behavioral intelligence required to identify the most elusive risks early. DTEX InTERCEPT™ ingests high-fidelity data from cyber-physical, psycho-social, and organizational sensors to surface true positives with ample time to mitigate.
DETER
Be proactive
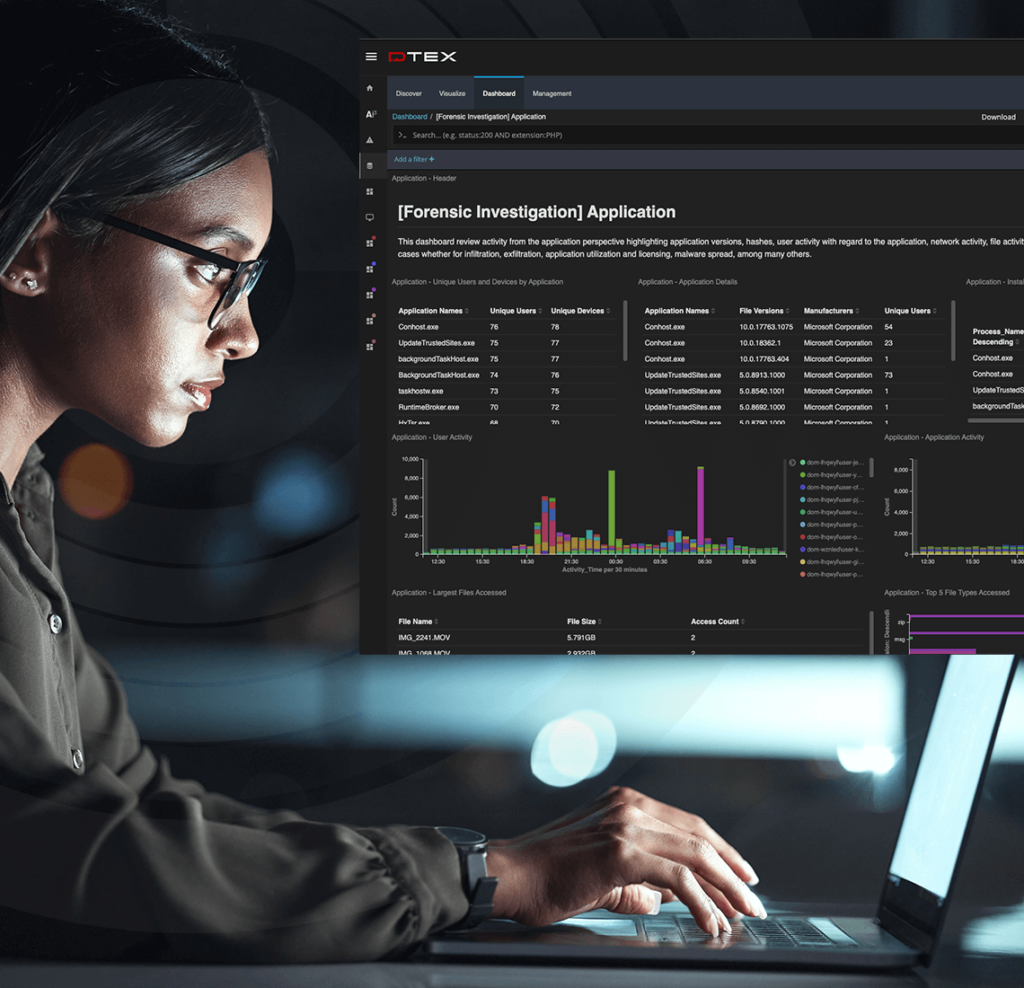
Harness the data gravity of DTEX InTERCEPT™ to understand behavioral intent and apply a proportionate response. Leverage out-the-box rules, detections, and mitigations to address some of the most complex use cases, including those that involve an external or third-party nexus.

DISRUPT
Stay resilient
Stop insider risks from becoming threats, and threats from becoming major security incidents. Only DTEX provides the behavioral telemetry, forensics, and expertise to support escalation, investigations, and, where relevant, prosecutions, so you can stay protected.
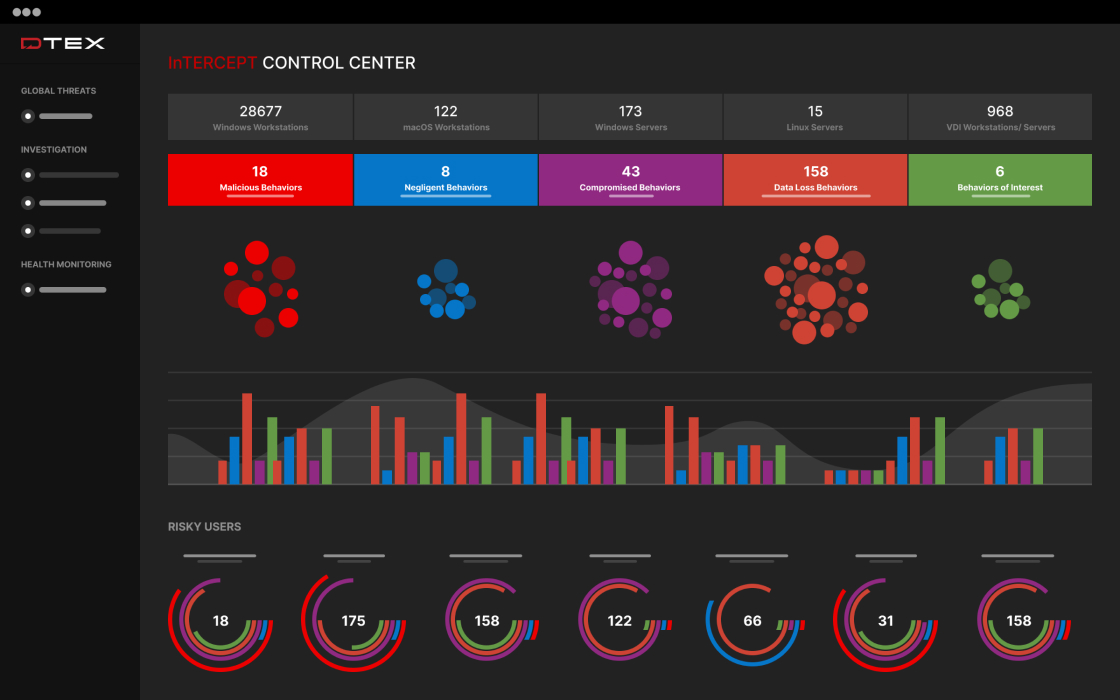
Context to counter every insider risk profile
Just because an insider does something unusual doesn’t make them malicious. DTEX brings you unrivalled insights to distinguish the different types of insider risks, so you can take appropriate action in support of a trusted and protected workforce.
MUST-KNOW INSIGHTS
DTEX i³ 2024 Insider Risk Investigations Report: Foreign Interference, Special Edition

Stay resilient against foreign interference