Next-gen Insider Risk Management and Behavioral Data Loss Prevention
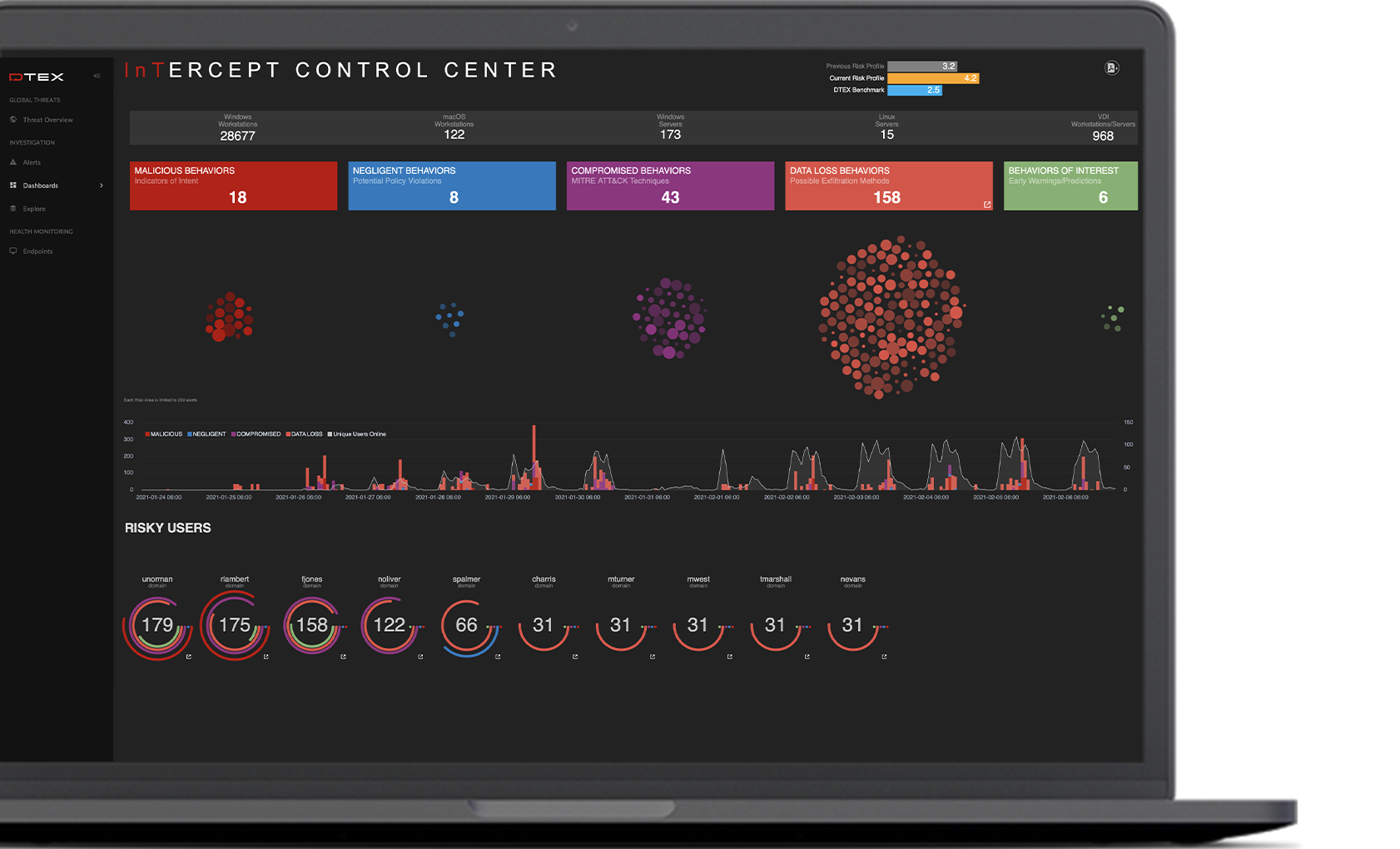
DTEX InTERCEPT consolidates the essential elements of Data Loss Prevention, User Behavior Analytics, and User Activity Monitoring in a single light-weight platform to detect and mitigate insider risks well before data loss occurs. Combining AI/ML with behavioral indicators, DTEX enables proactive insider risk management at scale without sacrificing employee privacy or network performance.
InTERCEPT is a scalable, cloud-native platform. Through its patented and privacy-compliant metadata collection and analytics engine, the DTEX platform surfaces abnormal behavioral “indicators of intent” to mitigate risk of data and IP loss, enabling SOC enrichment with human sensors and empowering enterprises to make smarter business decisions quickly.
Smart, Sophisticated, Scalable Workforce Cyber Security
What the SANS Institute™ thinks about DTEX InTERCEPT
There’s one common weak point among every digital enterprise in the world. Whether your organization provides healthcare, processes financial transactions or moves freight from one place to another, the least common denominator remains the same: the user.
Does this mean the user is inherently bad or security is destined to fail? Quite the opposite. It means users need different types of protection so that security has a fighting chance to succeed. In this white paper, SANS Institute analyst Matt Bromiley reviewed DTEX InTERCEPT and recognized it as a platform that seems to have taken that statement to heart.

The latest on Insider Risk Management

SANS Product Review: Smart Enterprise Visibility with DTEX InTERCEPT
Download this report from SANS for an assessment of how DTEX InTERCEPT can help your organization achieve its security objectives.
Read More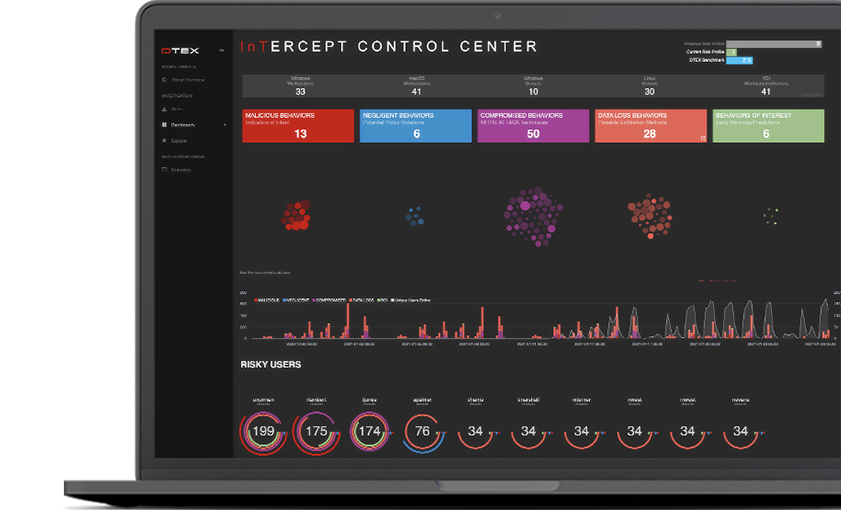
DTEX InTERCEPT 6.0 Demo
Watch this on-demand webinar to learn more about ‘Dtex Intercept 6.0 – The Next-Generation of Insider Threat Management.’…
Read More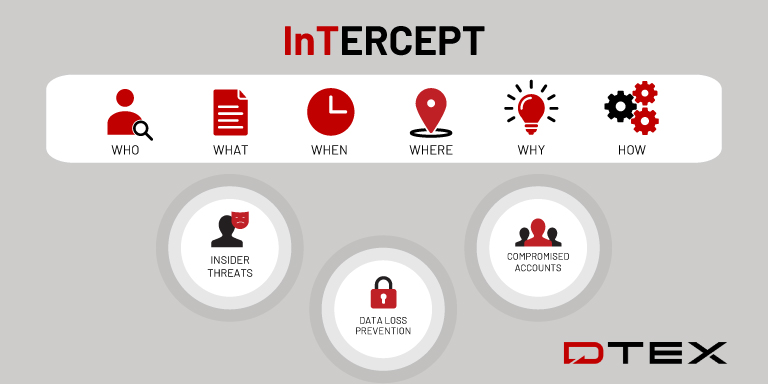
DTEX InTERCEPT Workforce Cyber Security
DTEX InTERCEPT™ brings together the capabilities of Insider Threat Management, User and Entity Behavior Analytics, Digital Forensics, and Behavioral Analysis…
Read More


