- Build rapport with the various teams involved in your organizations’ offboarding process. Formalize processes to increase visibility of company leavers and solidify the role of the Insider Risk Management (IRM) program.
- Identify high-risk user groups and apply technical controls, to focus detection minimize the organizational attack surface. Focusing monitoring and detection capabilities on high-risk user groups makes efficient use of often limited organizational resources.
- Identification and sensitivity labelling of crown jewels (critical data) within the organization allows for active monitoring of sensitive information.
- Increase employee awareness of the IRM program. Proactively making employees aware of a program that is in place to protect them and the business and establishing a formalized point of contact for reporting suspicious activity or behavior helps create a culture of transparency, vigilance, and accountability.
- Leverage behavioral analytics and mitigation controls that are in proportion to the level of user risk (for example, “teachable moments” for non-malicious users and focused observation for malicious users) and capture detailed audit trails.
INTRODUCTION
Customers have been reaching out for more guidance in cases that involve foreign interference, especially with recent high-profile incidents involving theft of trade secrets. This Insider Threat Advisory (iTA) presents a real-world investigation involving the early detection and mitigation of foreign interference in a customer environment. Importantly, the advisory provides critical behavioral indicators and mitigations for detecting, deterring, and disrupting malicious behaviors associated with espionage and IP theft.
By applying the indicators and mitigations, organizations can proactively reduce the potential for data exfiltration, protecting their competitive advantage, brand, and bottom line. This iTA will also discuss important considerations for maturing an IRM program and highlight other helpful mitigations that exist outside of IRM technology.
For context, the target organization was a large technology company with a mature cybersecurity program and an established response structure for handling security incidents.
The height of stealth, “blended attacks”
The DTEX i3 2024 Insider Risk Investigations Report, released annually, highlights trends around insider threats based on our customer investigations around the globe. This year’s report focused on foreign interference, with insight into the socially engineered insider and intersection with espionage. The 2024 report findings support the conversation surrounding the rise of blended attacks, where sophisticated threat actors are employing multiple internal and external tactics to achieve their mission. This includes disguising activity as part of the “normal” activity of the organization.
Detecting super malicious insider threats, like those associated with foreign interference via social engineering, is particularly challenging, especially when compared with other vulnerabilities and threats. This is because there is no silver bullet to detecting psychological manipulation of what otherwise appears to be legitimate, authorized activity. A compromised insider colluding with an external adversary could easily go unnoticed by virtue of their authorized access and actions, particularly if those actions are considered to be “normal” by the organization.
The complexity of insider threats underscores the importance of a dedicated IRM program that cuts across people, unified and integrative technology, processes, and people; without this, sophisticated insider threats, such as the example described above, can easily fall through the cracks.
REAL-WORLD SCENARIO
A DTEX customer requested an i3 investigation into a user for possible data exfiltration. The company’s legal department initiated a full review into the end user’s behavior and to identify evidence of exfiltration (attempted or successful) as well as evidence of travel plans to China. The customer, already aware that they would be a target for foreign interference, were vigilant for indicators of such activity.
Initial analysis of escalated behavior suggested the user may have been involved in potential data exfiltration through the browser; the user had interacted with their personal email and deleted files. While each activity on its own may seem harmless, when correlated in the context of the Insider Threat Kill Chain, the risk quickly morphs into a threat. Collectively, the user’s actions were indicative of malicious intent in that they were actively employing countermeasures to avoid detection.
The DTEX i3 investigator was able to piece together the exfiltration activity and uncover other red flags, including data aggregation prior to exfiltration. The user copied 3.9GB of sensitive data and uploaded it to their personal OneDrive account via Google Chrome.
The data visualization below demonstrates the user’s aggregation of data into the “New folder” folder on their desktop.
Logs obtained via DTEX InTERCEPT also captured the user’s interaction with Google Chrome, detailing their access and connection to the sanctioned OneDrive. The below figure shows how DTEX InTERCEPT will resolve the host name to the IP address, allowing insider threat practitioners to stay within the platform. Further review of the OneDrive logs by the customer confirmed the user logged into a non-corporate account prior to the exfiltration events. This confirmation of the personal OneDrive was validated through collecting a disk image.
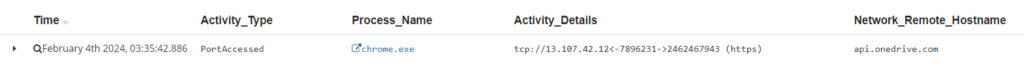
Chrome showing the PortAccessed activity for connection the OneDrive API.
As an aside, DTEX InTERCEPT now has a more accurate feature to monitor and detect exfiltration and downloads, and even potentially the account used, personal or corporate (depending on the file hosting service) via the HTTP Inspection Filtering (HIF). For more information on this feature, then please reach out to your DTEX point of contact.
Users demonstrating additional behaviors could indicate a higher potential of becoming an insider threat. Flight risk behavior is a powerful indicator; users looking for another job, scheduling interviews, or submitting applications have a higher risk of departing from the organization. The increased risk of departure can serve as an early warning indicator to implement additional monitoring or add the user to the Persons_of_Interest named list in DTEX InTERCEPT to systematically heighten the user’s risk score and investigative priority.
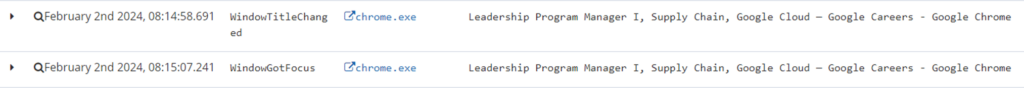
Flight risk behavior. Columns are time of activity, activity type, process, window title.
The files exfiltrated by the user were primarily related to suppliers, shortage reports and backlog reports – all of which aligned with the types of jobs the user was looking for.
Additional investigation into the user’s activity confirmed the documents were confidential in nature, and directly related to the positions the user was researching. Over 600 unique files were identified by DTEX InTERCEPT as having been exfiltrated from the organization. By using the DTEX InTERCEPT audit trail, a comprehensive list of all files was generated from the aggregated data in the desktop folder.
After having aggregated the data, the user employed forensic countermeasures to try and hide their activity by using a non-corporate OneDrive as well as deleting the aggregated files. These individual behaviors are commonly exhibited by risky insiders and are a common pattern observed during insider threat events.
Once the analysis of the logs was complete and the evidence was gathered, the company’s IRM team handed the investigation over to the legal department. The evidence provided included the DTEX InTERCEPT audit trail, digital forensic evidence from the disk image, and cloud-based logs.
This content is classed as “limited distribution” and is only available to approved insider risk practitioners. Login to the customer portal to access the indicators or contact the i³ team to request access.
EARLY DETECTION AND MITIGATION
The DTEX i3 team recommends organizations implement the following controls to detect, deter, and disrupt insider threat activity associated with foreign interference.
Business security starts with understanding the threat profile. This involves identifying the core value of the business, recognizing market competitors, and assessing potential threats, including foreign interference, based on threat intelligence. This understanding enables the prioritization and enhancement of security programs by developing detection indicators and mitigations against blended attacks from foreign interference or other external threats.
Offboarding processes and notifications
Foster relationships and open communication lines with the various groups involved in employee offboarding (particularly HR, IT, and insider risk teams). Communication of crucial information, like employee names and dates of departure, allow insider risk practitioners to prioritize review of identified users and their activity. Establishing processes and notifications for addressing the risks associated to offboarded users can also help reduce the likelihood of data exfiltration. In cases where offboarding is not expected, immediate communication across departments is critical to determine whether any negative impact on the business has occurred.
Identify high-risk user groups and apply technical controls
Identifying high-risk user groups – such as, engineers, executives, employees with access to patents, or sudden company leavers – can help focus the often-limited resources of an organization. This goes along with the next mitigation of identifying the crown jewels of your organization to better understand which users have regular access to the data and may abuse their access, becoming insider threats, or those that may be targeted by external threat actors.
Preventing the use of personal accounts, especially on organizationally approved applications, can also significantly reduce the threat profile. This prevents misuse and provides insider risk practitioners improved visibility of exfiltration activity.
Identify crown jewels
Identify the crown jewels (or critical data) within the organization and ensure sensitivity labelling is applied.
Monitoring for activity surrounding the crown jewels is not only the responsibility of the IRM program but should also be prioritized by the information security program as a whole.
In cases where an organization does not have an understanding around crown jewels, DTEX recommends utilizing the InTERCEPT behavioral-based sensitivity model for insights around potentially sensitive documents within the organization at scale.
Educate employees
Educate users that about the company’s IRM program, how it affects them, how they can contribute to the security of the organization and data and, most importantly, why they should care. Being transparent that there is a program in place to protect the business, the employees, and in some organizations, national security, can be a powerful deterrent. Those that would attempt malicious actions regardless can then be prioritized, helping security teams to remain focused on genuine threats. This should also include a formalized process of reporting any suspicious activity or behavior (“See something, say something”). The MITRE Insider Threat Research & Solutions addresses the need for this employee reporting mechanism and potential solutions for countering employee concerns around anonymity of reporting. MITRE’S upcoming Insider Threat Framework will provide further recommendations when released. For now, this could be achieved through an anonymous tip line that could be managed by a third party.
Implement insider threat monitoring and detection
Leverage behavioral intelligence, analytics and mitigation controls that are in proportion to the level of user risk (for example, “teachable moments” for non-malicious users and focused observation for malicious users) and capture detailed audit trails. Integrating these features enriches SOC operations and provides scalability to all enterprises.
CONCLUSION
Effective protection against foreign interference requires a multi-faceted approach with defense-in-depth. A robust IRM program is imperative and requires close collaboration among business units such as HR, Finance, Privacy, and Engineering, alongside established processes and strong leadership commitment.
In this incident, the integration of tagged end-user activities and alert generation enabled seamless teamwork across various departments. This proactive approach and adherence to established policies led to the timely detection of data exfiltration and allowed legal investigators to impose consequences on the malicious insider.
To maintain and enhance your security posture, it is crucial to continuously evolve your environment in line with your dynamic business and security landscape. Implementing the recommended mitigation strategies and collaborating with DTEX i3 team are vital steps toward strengthening your defenses against insider threats.
INVESTIGATIONS SUPPORT
For intelligence or investigations support, contact the DTEX i3 team. Extra attention should be taken when implementing behavioral indicators on large enterprise deployments.
RECOMMENDED READING
DTEX i3 2024 Insider Risk Investigations Report
How Behavioral Intelligence Can Counter Foreign Interference
The Rise and Stealth of the Socially Engineered Insider
The Rise of AI and Blended Attacks: Key Takeaways from RSAC 2024
Get Threat Advisory
Email Alerts






