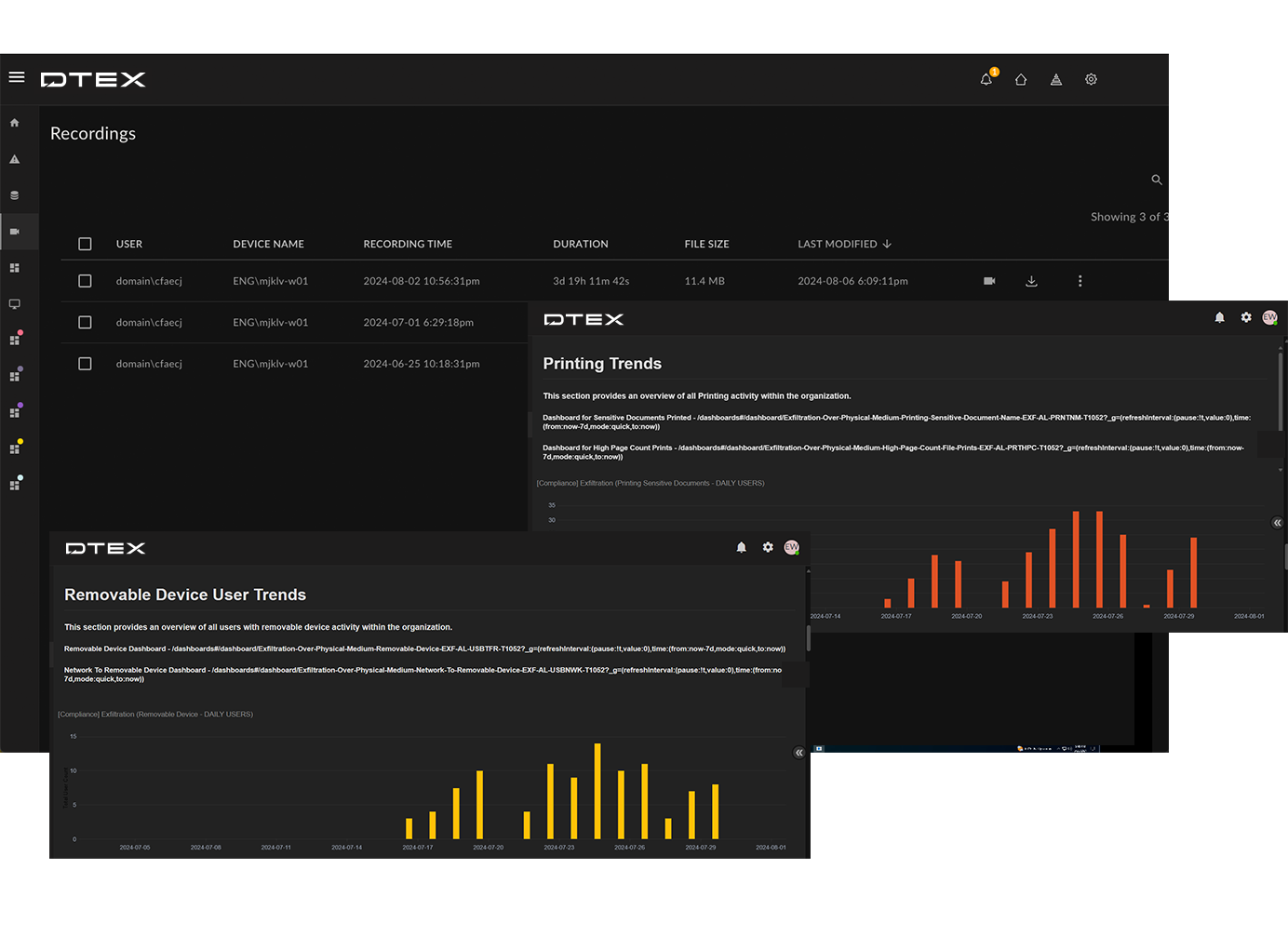
What is focused observation?
Increase monitoring and alerting mechanisms for high-risk populations and identify activity attempting to avoid detection.
Malicious intent
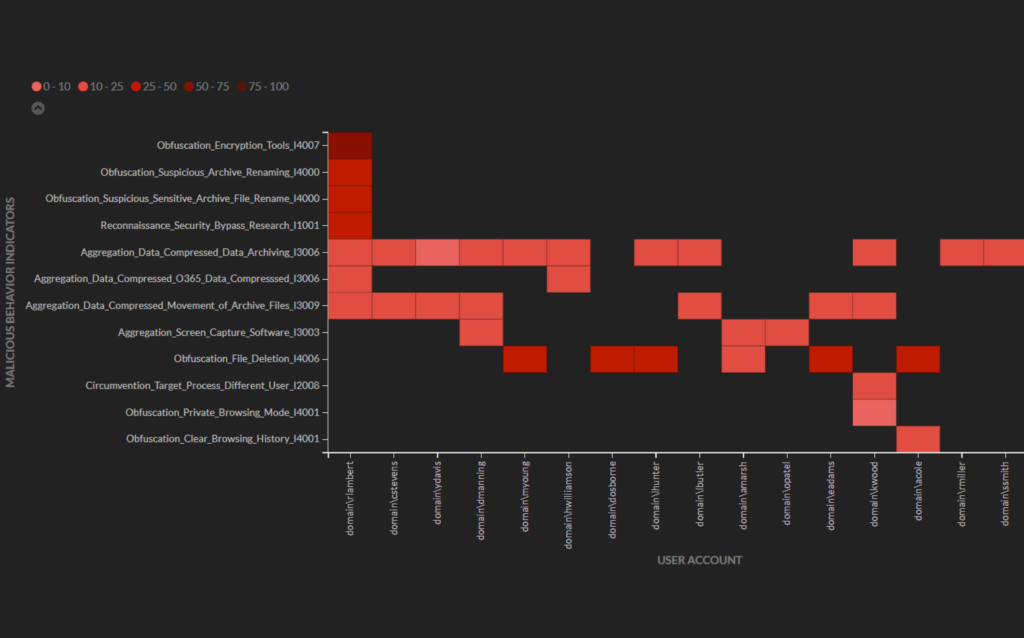
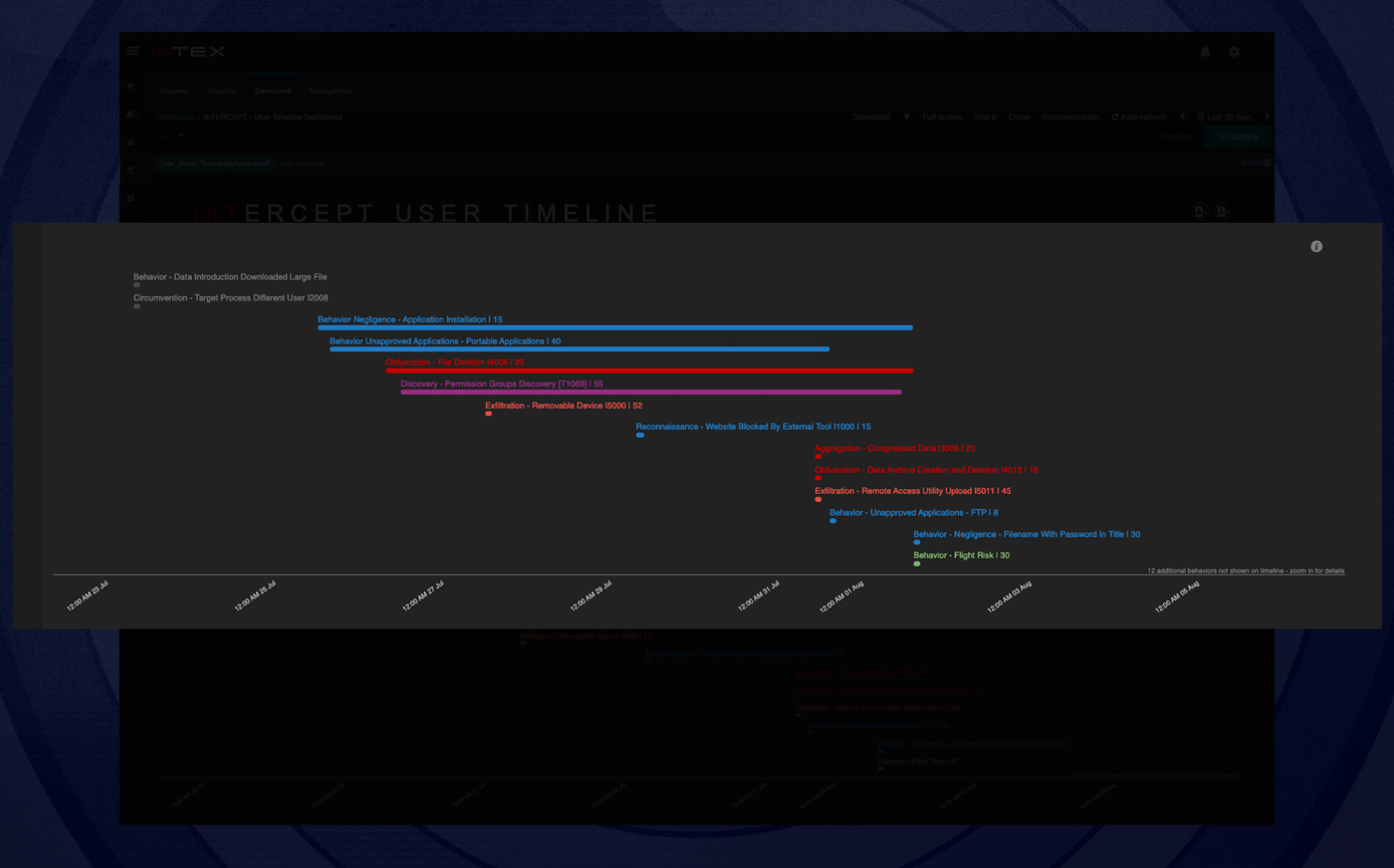
Obfuscation activity
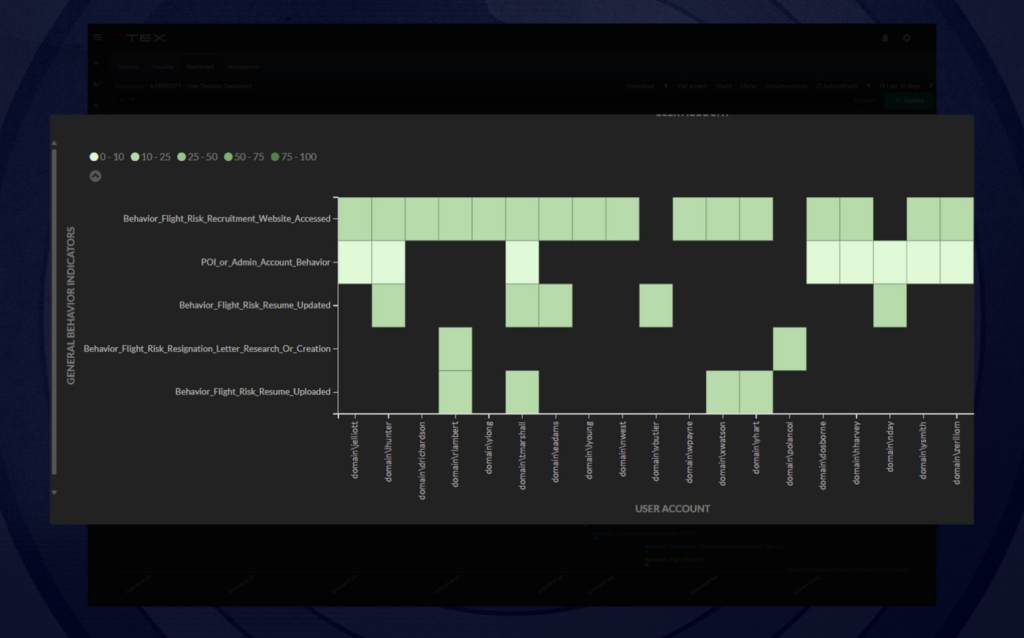
Flight risk indicators
KEY RESOURCES
DTEX Insider Risk Management and the Department of Defense Zero Trust Strategy

Early detection is the holy grail
DTEX proactively identifies risk to provide the benefit of time to course correct before an incident occurs.