Network security professionals have long relied on “Indicators of Attack” and “Indicators of Compromise” to identify malicious attacks early. A solid strategy to be sure as this approach offers lots of raw data about machine and application processes that can be used to implement simple protection triggers. Unfortunately, these simple triggers are a shortcoming of UEBA technologies and routinely result in false positives and false negatives that block proper activity, leave SecOps swimming in a lake of raw data, and leave IR pro’s searching for answers to questions like Who, What, When, Why, Where and How?
UEBA to the rescue?
UEBA solutions attempted to answer these questions by developing and packaging useful models for analysis and alerting. But there was one problem: their implementation relied on log files, which are a flawed data source for capturing user behavior.
When protecting organizational IP it is important to identify user activities alongside IoC’s and IoA’s that are precursors to exfiltrating data. These “Indicators of Intent” are identified by observing and correlating activities associated with earlier stages in the attack kill chain.
Sounds simple right? Yes and no. It requires collecting, enriching, and correlating hundreds of unique activities across thousands of users and applying statistical analysis and machine learning to execute properly.
UEBA + Indicators of Intent – Now we’re cooking!
Truth is, monitoring for ‘Indicators of Intent’ simplifies an organization’s defenses and enhances your UEBA strategy. It doesn’t complicate it. Rather than attempting to classify every piece of data and role-based rules for legitimate use, ‘Indicators of Intent’ enable organizations to monitor all activities by all users (while protecting user privacy) and to alert on suspicious, anomalous and known-bad activities before data exfiltration is attempted. No log files, no role-based rules, no false negatives or positives, no lengthy forensic investigations and no lost data.
In this blog series we will explain DMAP+ Technology (Data, Applications, Machines, and People) and how these “indicators of intent” enhance UEBA. You will learn how DMAP+ works (on the endpoint), what it collects (meta-data) and what it observes and records (on and off the network) to prevent data loss caused by malicious insiders, compromised users and negligent third parties.
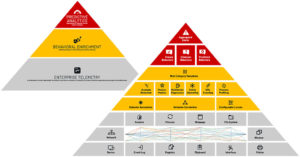
Enterprise Telemetry: Source of User Activity Data
Let’s start by defining enterprise telemetry and what it means to capture the user activity data that matters. The Enterprise Telemetry layer of DMAP+ contains a combination of smart, lightweight forwarders that capture and correlate real-time telemetry from data, machines, applications and people. All activity group types such as session, process, file system, window, net-flow, webpage, network, device and other activities are continuously streamed to the cloud for behavioral enrichment and predictive analysis… more to come on that in part 2. For now, let’s dive into activity group types.
User Session Activities – Each user session is logged and analyzed to identify anomalous, unsafe and malicious activities. This includes anomalous session access and shared logins that may indicate credential theft, unusual working hours, the use of decommissioned accounts or privileged accounts in abnormal ways.
Process Activities – All activities on the endpoint trigger a process that can be recorded and analyzed, including process hash (MD5, SHA1 or SHA256), process parent and child relationships, application versions, execution paths and command line execution parameters.
DMAP+ uses this to identify ‘Indicators of Intent’ such as the unauthorized use of hacking tools (password crackers, network sniffers), attempts to bypass of security controls, the use of non-sanctioned software, unusual application behavior, and attempts to obfuscate activity by using ToR and Proxy Bypass applications.
DMAP+ uses this to identify “Indicators of Intent” such as the unauthorized use of hacking tools (password crackers, network sniffers), attempts to bypass security controls, the use of non-sanctioned software, unusual application behavior and attempts to obfuscate activity by using ToR and Proxy Bypass applications.
File System Activities – Attackers typically start by identifying sensitive data (Reconnaissance) followed by disguising (Obfuscation) and centralizing it (Aggregation) before attempting to exfiltrate data. Obfuscating data can include simply renaming a file or changing a file extension of a customer list from xslx to jpg. Data aggregation would involve large numbers of downloads or transfers between systems within the organizations (lateral movement). DMAP+ captures all relevant metadata about files such as ADS and document properties that include file classification markings, allowing it to focus on sensitive data. DMAP+ tracks the lineage of every file as it moves through the organization across different endpoints, effectively exposing attempts to disguise and aggregate data.
DMAP+ tracks all use of all data to identify actions that prevent data theft. This includes creating, populating, moving and deleting files and directories, activities designed to inhibit tracing of data and forensics, and unauthorized system configuration changes.
Net-Flow Activities – While data can be exfiltrated by downloading to a portable drive or even printing the desired information, it is common for criminals to use network connections to remove data. Most traditional DLP solutions focus on the final step in the kill chain – exfiltration of large amounts of data, FTP and SCP file transfers, and uploads to cloud storage that can identify a completed attack. While DMAP+ also alerts on this action, it also focuses on activities required to prepare for exfiltration. This includes moving anomalous amounts of data laterally across the network, aggregating data to unusual network locations and the usage of rogue or unauthorized applications (e.g., anonymous proxies).
Webpage Activities – Searching recruiting websites and frequent updates to LinkedIn profiles can provide an early indication of employee flight risk, therefore warranting increased scrutiny on the use of sensitive data. Likewise large uploads to webmail or file sharing accounts can provide an “Indicator of Intent”. DMAP+ tracks all web activity, including the full webpage URL for http and https websites, and domain and page title information correlated with web browser.
Network Interface Activities – DMAP+ tracks all network connections, on and off the corporate network. It captures Wi-Fi SSID and public IP information for geolocation to identify suspicious activity over public Wi-Fi, VPN disabling and all actions after logging on or off a network.
Device Activities – Removeable storage devices like SSD and thumb drives are popular exfiltration tools because they hold large amounts of data but still can be easily hidden in briefcases and pockets. DMAP+ identifies when these devices are attached to a system and all data activity associated with the devices. In addition, DMAP+ can alert on user actions that may precede data exfiltration, including connections to wireless Bluetooth or AirDrop devices.
Windows Event Log Activity – An attacker or compromised employee may create additional user accounts or change privileges for an individual or group. DMAP+ monitors all Windows event logs to identify indications of activity that could precede an exfiltration, including credential misuse, changed firewall or security settings and changes in privileges or group policies.
Windows Registry Activity – An attacker may attempt to bypass security controls by changing system configurations. DMAP+ captures all Windows Registry modifications (e.g., query, create, modify, delete) for configured registry directives as well as high-risk registry modifications and tampering with system settings.
Clipboard Activities – Copy/paste is a simple way to capture data in preparation for an exfiltration attempt. DMAP+ has visibility into all endpoint activity, including any data copied to or pasted from the clipboard. By correlating the content hash with the user and source/destination processes, DMAP+ provides early indicators of malicious intent.
Print Job Activities – As previously noted, physical exfiltration of sensitive data can be just as damaging as electronic exfiltration. A user printing a large quantity of sensitive information on local or remote printers or printing during unusual hours can be an indicator of an attack in process.
Window Activities – When preparing to steal data, the attacker may need to continuously switch between applications, copying data from one into the other. DMAP+ observes task switching “window” behavior in context, and correlates this with the underlying user account and role, process and application (Webmail, file sharing or anomalous usage), and device to identify malicious “Indicators of Intent”.
Enterprise telemetry is the foundation of DTEX’s DMAP+ Technology and makes it possible to deliver a 24x7x365 continuous audit trail of unique endpoint metadata to observe and record the actions and activities of data, machines, applications and people (DMAP) in near-real-time, both on and off the corporate network to surface dynamic behavioral awareness indicators. This is an advantage that traditional UEBA technologies do not apply. In part 2 we will review Behavioral Enrichment and Predictive Analytics.
Subscribe today to stay informed and get regular updates from DTEX Systems





