In part one of this blog – The Road to UEBA Redemption: Identifying Indicators of Intent – we explained the Enterprise Telemetry layer of DMAP+ as a combination of smart, lightweight forwarders that capture and correlate real-time telemetry from data, machines, applications and people. We reviewed how it works (on the endpoint), what it collects (meta-data) and what it observes and records (on and off the network) to prevent data loss caused by malicious insiders, compromised users and negligent third parties.
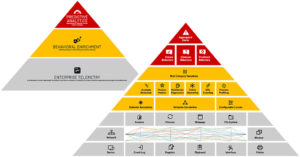
In this second blog, we will dive into the second and third layers of our DMAP+ Technology – Behavioral Enrichment & Predictive Analytics — to explain how enterprise telemetry is synthesized, enriched and analyzed using advanced behavioral machine learning frameworks and community-proven artificial intelligence to help IT and SecOp pro’s answer questions like Who, What, When, Why, Where and How?
Behavioral Enrichment — Data Without Intelligence is Noise
Security tools – especially UEBA tools — are notorious for verbose output that can obscure the results on which security analysts should focus. This is why many are simply left in “monitor mode”. Unfortunately, this allows adversaries to continue their attacks until security sifts through results to (hopefully) identify indicators of an attack.
The second layer of DTEX DMAP+ Technology enriches the raw data from activity monitoring with insights from behavior analytics, risk profiling, and machine learning to expose Indicators of Intent; before an attack can be completed.
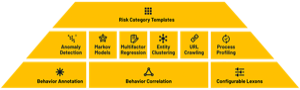
The techniques used in the DMAP+ platform enables the solution to discern between legitimate activities and malicious intent. Two important stages of behavioral enrichment are Activity Annotation and Activity Correlation.
Activity Annotation processes activities through known behavioral profiles. This tags activities that appear anomalous for a particular user, role, data set, device, and other variables based on “known good” and “known bad” templates. Activities of interest will undergo additional behavioral analysis and anomaly detection routines.
Activity Correlation applies ‘correlation logic’ on a series of actions to cut through the noise and create a higher-level activity based on the expected sequence of activities, the expected time window, the linking data elements and a specified rule trigger.
Unlike traditional UEBA, Insider Threat and Endpoint DLP solutions, DTEX DMAP+ does not rely on customized and complex policies to detect malicious activity. Its rules, patterns and logic codify DTEX’s deep domain knowledge; similar to what a team of insider threat experts would bring to an organization. By applying this domain knowledge to raw activities, DTEX surfaces anomalous behavior relevant to data exfiltration attempts for further analysis in the Analytics Module.
Predictive Analytics — Don’t Wait for Data to Leave
Armed with preprocessed behavioral data, DTEX’s DMAP+ Predictive Analytics engine can focus quickly on those combinations of activities indicative of an attack – before the attack is completed. With DTEX’s domain knowledge, false positives are minimized, and legitimate use of data continues uninterrupted.

Waiting until an attacker has exfiltrated data to alert security makes security reactive. The data theft kill chain requires attackers to take a number of steps to find and aggregate data, test and bypass security controls, and hide their actions before exfiltration begins.
Provided with complete activity information, behavioral context, and predictive analytics, DTEX DMAP+ processes and tracks the artifacts produced by these steps – in context with the users, roles, data, and devices – to spot ‘Indicators of Intent’ and stop attacks long before exfiltration attempts are practical.
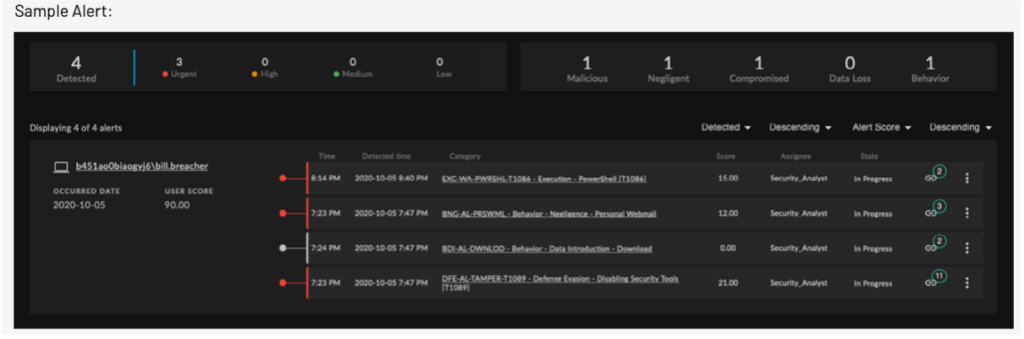
Aggregation of risk scores and alert stacking provides actionable information regarding known and unknown insider threats. Outputs from the alert stacking algorithms can also be integrated into 3rd party SIEM platforms and data lakes.
In fact, DTEX’s DMAP+ Technology complements SIEM systems to produce a consolidated and transparent view of user activity and intent. SIEM systems consolidate a substantial volume of data from logs – which can result in an overwhelming number of events. By contrast, DTEX uses analytics to pinpoint the most relevant events. In addition, SIEM systems – while sophisticated in their capability to collect, integrate and analyze data from multiple disparate sources – do not necessarily have visibility into user activities on endpoint devices. You can learn more about how we compliment SIEM technologies.
Subscribe today to stay informed and get regular updates from DTEX Systems





