On Wednesday, March 23rd the National Counter-Intelligence and Security Center (NCSC) issued updated insider threat mitigation guidelines for all United States Critical Infrastructure entities.
According to the National Counterintelligence & Security Center’s latest report titled ‘Insider Threat Mitigation for U.S. Critical Infrastructure Entities – Guidelines from an Intelligence Perspective’ ‘foreign adversaries are no longer simply targeting the U.S. government, as was often the case during the Cold War, but today are using their sophisticated intelligence capabilities against a much broader set of targets, including U.S. critical infrastructure and other private sector and academic entities. These U.S. industry and academic organizations are now squarely in the geopolitical battlespace.’
Based on this evolving threat landscape, the NCSC report directs critical infrastructure entities to prioritize and dedicate resources to preempt and mitigate insider threats. Insider threats, as defined by the NCSC report and the National Insider Threat Task Force (NITTF) are ‘trusted individuals in an organization who may use their authorized access to facilities, personnel, and information to cause harm to their organization — whether intentionally or unintentionally.’
Similar to other reports issued in December 2020 by Gartner, Inc and in February 2021 by Forrester Research, the NCSC report issued last week, calls attention to the need for organizations and cyber security teams to understand workforce behavior and gain the visibility to recognize anomalous activity.
To help mitigate insider threats, both from insiders working with external actors and trusted insiders who have been unknowingly compromised, an organization must, at a minimum, achieve two things according to the NCSC:
- ‘Have a program that identifies individual anomalous behavior and the resources to respond.
- Respond to anomalous behavior in a way that fosters trust and leverages the workforce as a partner.’
Insider Threat Kill Chain & Identifying Anomalous Behavior
The vast majority of security threats follow a pattern of activity during an attack, and insider threats are no exception. Many security professionals will already be familiar with Lockheed Martin’s Cyber Kill Chain, which outlines the steps that APT attacks tend to follow from beginning to end. Since human behavior is more nuanced than machine behavior, however, insider attacks follow a slightly different path. Over the course of thousands of insider threat investigations and incidents, DTEX analysts have identified the insider equivalent: The Insider Threat Kill Chain, which encompasses the five steps present in nearly all insider attacks.
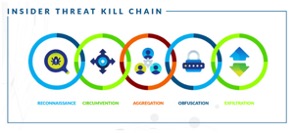
In order to fully understand any insider incident, visibility into the entire kill chain — not just one or two steps — is imperative. This is because the earlier phases of the Kill Chain hold the answers to some of the most important questions – both for incidents that have yet to fully unfold and for those that have already occurred.
These include:
- What was the intent of this user? Was this an accidental breach or a calculated attack?
- Was this truly an insider, or were this user’s credential compromised by an infiltrator?
- If this was a case of stolen credentials, how did the credential thief get into the account?
- Did a security misconfiguration allow this to happen?
- What other files were affected?
At DTEX, we provide organization-wide user visibility that shows you every step of the kill chain, rather than just focusing on the moment of exfiltration. To learn more about the Insider Threat Kill Chain, check out my blog series or download our eBook on the topic.
Free Insider Threat Assessment for Critical Infrastructure Entities
DTEX is now offering a comprehensive ‘Insider Threat Assessment’ that identifies and analyzes a Critical Infrastructure entities insider risk posture and data loss vectors across common user activity and behavioral categories. The trial is 100% commitment free and available to all energy, water, telecommunications and healthcare organizations with headquarters in Five Eyes countries.
This assessment will provide a thorough review of the NSCS’s Nine Elements of Insider Threat Programs for Critical Infrastructure Entities including direct evaluation of an organization’s maturity against the NITTF Insider Threat Model used by the U.S. Department of Defense and the Department of Homeland Security (DHS). An actionable, easy-to-read report will be delivered and reviewed by DTEX solution architects following the 30-day engagement. Click here to request a free assessment.
Subscribe today to stay informed and get regular updates from DTEX Systems






