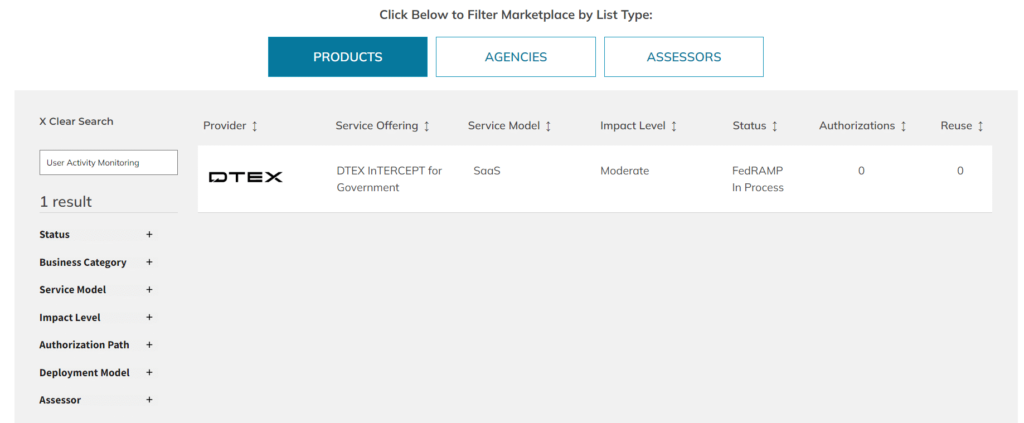
DTEX is on track to deliver the first and only solution meeting the CNSSD 504 User Activity Monitoring (UAM) directive on the FedRAMP Marketplace. In a major win for federal insider threat practitioners, DTEX has received FedRAMP “In Process” status with its InTERCEPT™ for Government platform.
To date, federal agencies have only been able to obtain the platform for on-premises environments. Once FedRAMP authorization is complete, agencies will be able to obtain, procure, and utilize InTERCEPT for Government as a hosted service without the cost and burden of having their own infrastructure.
The designation is good news for federal entities that must meet strict UAM requirements set by the National Insider Threat Taskforce under CNSSD 504, as they will soon be able to do so easily through the cloud.
Introduced in 2014, these requirements are designed to detect indicators of insider threat behavior and require the technical capability to observe and record individual actions on any device accessing U.S. Government information at any time.
To date, no solution or tool that meets the CNSSD 504 standards are available on the FedRAMP Marketplace. But this is set to change.
DTEX InTERCEPT for Government
With the FedRAMP authorization process now well under way, DTEX is poised to fill this critical gap. DTEX InTERCEPT for Government is a SaaS offering that integrates Data Loss Prevention (DLP), User and Entity Behavior Analytics (UEBA), and User Activity Monitoring (UAM) to detect and mitigate insider risks before data loss occurs.
In addition to mapping to all UAM must-have requirements of CNSSD 504, DTEX InTERCEPT – which has built-in UEBA – also meets the recommended capabilities, including those outlined in Table 1. These are outlined in detail below.
Once authorized, FedRAMP will enable customers to leverage behavioral telemetry from InTERCEPT, employing data science and AI to detect early warning indicators and deter insider risks.
What is the National Insider Threat Task Force (NITTF)? and what are the CNSSD 504 requirements and recommendations?
The National Insider Threat Task Force (NITTF) was established in October 2011 by Executive Order 13587, under the joint leadership of the Attorney General and the Director of National Intelligence. Its creation was a direct response to the need for stronger protection of classified information across federal departments and agencies. The NITTF’s primary mission is to develop and implement a government-wide insider threat program aimed at deterring, detecting, and mitigating threats from insiders who may exploit, compromise, or disclose classified information without authorization. The NITTF assists agencies in creating and enforcing insider threat detection and prevention programs, ensuring these programs are tailored to the unique risks, missions, and systems of each agency.
What is CNSSD 504? What are the requirements and recommendations?
The Committee on National Security Systems Directive 504 (CNSSD 504) is a directive established in 2014 to protect U.S. Government information systems from insider threats. It mandates that all Executive Branch departments and agencies implement User Activity Monitoring (UAM) to observe and record individual actions on any device accessing U.S. Government information.
The directive outlines five essential technical capabilities for UAM:
- Keystroke monitoring
- Full application content capture (including email and chat)
- Screen capture
- File shadowing, and:
- The ability to attribute collected data to specific users.
CNSSD 504 also lists the following recommendations for a holistic insider threat program:
- Privacy information: potential to damage an individual’s reputation
- Should incorporate this data into an analysis system capable of identifying anomalous behavior that may provide indications of insider threat activity and support D/A investigative requests
- The events or indicators in Table 1 (categories of potential insider threat events or indicators on NSS) are recommended for consideration:
Table 1:
- Account change
- Authentication failure/anomaly
- Baseline anomaly
- Excessive activity
- Evidence tampering
- Exfiltration
- Malware
- Network traffic anomaly
- Privilege violation
- System configuration change
- User behavior anomaly.
CNSSD 504 ensures that federal agencies have the tools to detect, analyze, and respond to potential insider threats effectively.
How DTEX InTERCEPT meets CNSSD 504
CNSSD 504 focuses on “threat behavior” – the things insider threats do as part of the Insider Threat Kill Chain.
Focusing on malicious behavior allows security and compliance teams to identify Indicators of Intent to stop threats before they steal data or cause harm.
DTEX meets the UAM requirements of CNSSD 504 in the following ways:
> Capture of full application content
Identifying Indicators of Intent requires observing activities across Data, Machines, Applications, and People (DMAP). Our DMAP+ Technology™ provides a continuous audit trail of unique endpoint metadata to observe, record, and correlate the actions and activities of data, machines, applications, and people in near-real-time, including the full capture of all Session, Process, File System, and Window activities, on and off the organizational network.
> Screen capture and keystroke monitoring
When a user has been elevated for focused observation, DTEX provides application content monitoring (includes SSL inspection for web browser-based activities), video/screen capture and keystroke capture. Capture can be based on specific device, application, user rules, or for individuals flagged as “persons of interest.” All captures can be exported for further analysis.
> File shadowing
Malicious insiders will often attempt to disguise (obfuscate) their actions by changing file names or extensions. DTEX continuously tracks documents, even when names and locations have changed, using configurable hashing algorithms including MD5, SHA1 and SHA256. It can determine the ‘lineage’ of a file to answer who, what, when, where, and why was a file was copied, modified, obfuscated or exfiltrated. DTEX also tracks file classification metadata as well as the usage of the Alternate Data Stream (ADS) for advanced attempts to obfuscate data.
> Set triggers/alerts based on user activity
When a skilled insider wants to steal data, they often separate their activities into smaller steps over a period of time to avoid detection. Alerting on every activity (which could be benign) can result in alert fatigue. DTEX has partnered with MITRE Corporation to advance Five Eyes capability for insider threat and foreign interference detection and mitigation.
- Alert Stacking and machine learning capabilities combine behavioral rules and anomaly detection to reduce false positives and analyst overhead.
- Automated Activity Correlation allows multiple disparate events to be attributed to a defined sequence of events occurring within a given time window.
- This further improves true positive detection rates by elevating alert scores for events that occur sequentially across the full Insider Threat Kill Chain, over and above alerting rules triggered in isolation.
- DTEX also provides the ability to automatically increase monitoring and alerting mechanisms for high-risk user populations (e.g., new joiners, leavers or “flight-risk” detected employees and individuals flagged as “persons of interest”) and automatic correlation of these populations with insider threat related activities.
What about privacy?
In many regions, particularly outside the U.S., organizations must comply with strict employee privacy regulations. In these jurisdictions, the use of focused observation capabilities would typically be prohibited due to their potential to violate privacy laws.
DTEX takes a different approach from traditional User Activity Monitoring (UAM). For instance, DTEX InTERCEPT employs a patent-protected ‘privacy-by-design’ Pseudonymization™ architecture that enables the proportional deployment of focused observation capabilities where legally permissible, while still safeguarding employee privacy rights.
Accelerating insider threat capability maturity in the federal sector
The threat landscape is increasingly evolving, and insider risk management is the biggest opportunity yet for mission-critical entities of all sizes to leverage as part of a broader, proactive security resilience program.
Now more than ever, federal agencies need continuous monitoring capability to proactively protect their most sensitive assets and people.
For specific insights on how DTEX InTERCEPT for Government meets all the requirements under CNSSD 504, download our CNSSD 504 Requirements Mapping datasheet.
To find DTEX via the FedRAMP Marketplace, simply search “UAM” or “User Activity Monitoring”:
To learn more or to talk to a federal expert at DTEX, email us for a discussion.
Subscribe today to stay informed and get regular updates from DTEX Systems






