The 2025 Ponemon Cost of Insider Risks Report shows that insider risk management is turning the tide on insider threats.
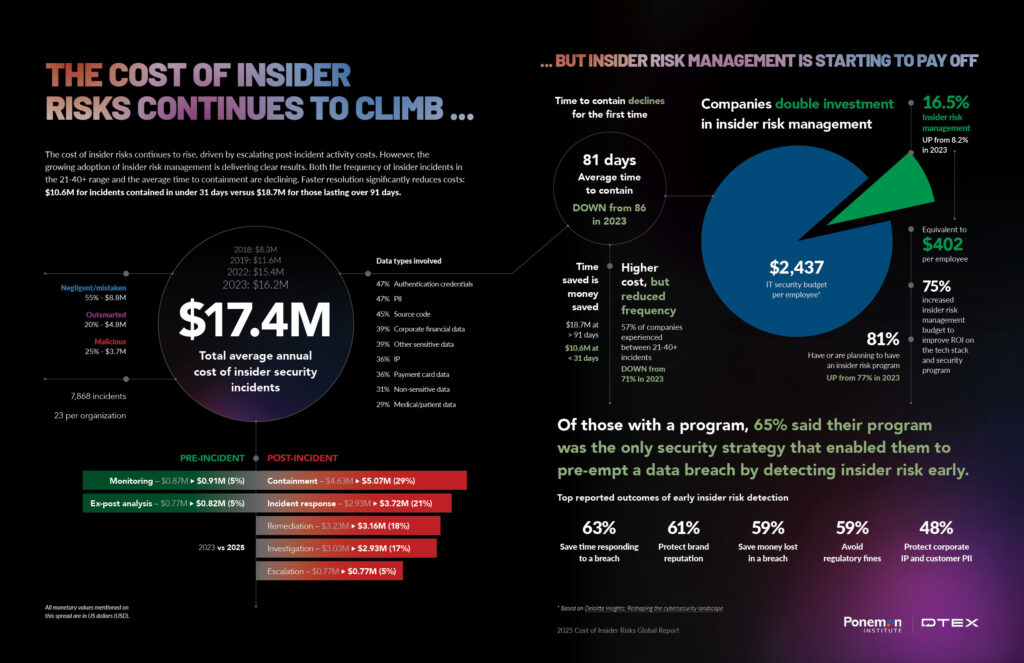
The cost of insider risk continues to rise, with the annual average reaching $17.4M – up from $16.2M in 2023 – largely driven by increased spending on containment and incident response.
But in a clear sign of progress, containment times have dropped (81 days, down from 86).
At the same time, companies are increasingly adopting insider risk management; budgets have more than doubled and those with an insider risk program are seeing clear results.
Based on 8,306 interviews with IT and IT security professionals, this year’s report is the largest yet and reveals first-time insights evaluating the effectiveness of these efforts, as well as sentiment around artificial intelligence, technology consolidation, and “blended attacks”.
Sponsored by DTEX, the report offers tangible findings for those on the frontlines needing to articulate the scope of the insider threat problem, and the cost versus opportunity of insider risk management solutions.
The following infographic provides the most salient takeaways:
Breaking it Down: What’s Working, What’s Not, and What Now?
Starting with what’s not working:
→ Companies are still spending disproportionately more money responding to insider security incidents than on measures designed to pre-empt and mitigate them.
For every insider incident, a company spends about $211,021 on containment, but just $37,756 on monitoring (pg. 32 of the report). The longer it takes to contain, the higher the cost: $18.7M for incidents contained in 91+ days, compared with $10.6M for contained under 31 days.
What now? To reverse this trend, companies must prioritize proactive strategies. As the report highlights, 65% of organizations with an insider risk management program said their program was the only security strategy that enabled them to pre-empt a breach by detecting insider risk early.
Breach prevention begins with early risk detection – emphasis on risk. If detection focuses solely on exfiltration, the chance to be proactive is already lost.
At its core, cybersecurity is a human challenge, requiring a human-centric approach. The key to proactive defense lies in an insider risk management program rooted in behavioral science. Organizations must understand the early warning indicators of risky behavior and have the right mechanisms in place to effectively detect and deter risks before they escalate into breaches.
→ Scaling security is hard. The larger the company, the higher the total annual average cost of insider risk – a staggering $26.2M for companies with a headcount between 25,001 and 75,000.
What now? Organizations must prioritize scalability of security solutions.
The non-negotiables for scalability:
- Enterprise-wide deployment: Does the solution work effectively across the organization without impacting performance? As the report reveals, insider risk extends far beyond privileged users or specific departments. In fact, the top three functions most vulnerable to exploitation by external adversaries are sales, HR, and marketing (pg. 14 of the report) – these areas are increasingly being targeted for their access to sensitive customer data, strategic plans, and proprietary information.
- Data integration: Does it integrate seamlessly with new and existing data sources?
- Automation: Does it automate detection and response at scale?
- False positive management: Can it reduce false positives as data grows?
- Customizability: Is it adaptable to evolving needs?
- Resource efficiency: Does it manage resources effectively?
- Real-time monitoring: Can it deliver real-time insights in complex environments?
- Efficient reporting: Does it generate actionable reports as data expands?
- Behavioral insights: Can it scale analysis of insider behavior patterns?
- Cost efficiency: Does it remain cost-effective as demands grow? Does it deliver ROI on the overall tech stack and cybersecurity program?
Moving onto what is working.
→ As stated above, the clear winner is the ability to detect risky insider behavior early. Companies that detect insider risk early report significant benefits, saving time, money, data, and reputational integrity that would otherwise be lost in a breach (pp. 12-13 of the report).
What now? Detecting risky behavior early hinges on quality data. When it comes to insider risk management, more data is not necessarily better. Importantly, cyber data alone is not enough. The right data cuts across cyber, physical, organizational, and psycho-social domains to afford the behavioral context needed to determine critical indicators of intent. Knowing what to look for and staying agile to change is also key, especially with the rise of AI misuse and evolving cyber espionage tactics.
→ Technology consolidation is also playing its part, affording companies cost savings, reduced complexity, faster detection, scalability, and actionable data (pg. 15 of the report).
A recent report by Forrester echoes these benefits, finding that companies were able to achieve $3.29M in tech stack savings over three years by retiring legacy data loss prevention, user activity monitoring, and user and entity behavior analytics tools.
Another noteworthy stat from the Ponemon Report: 75% of companies that increased investment in insider risk management did so to improve ROI of the tech stack and security program.
What now? Companies needing to prove ROI should strongly consider an insider risk management platform that consolidates the essential capabilities for early insider risk detection at the speed and scale required by the organization.
→ AI: No surprises here, but AI is seriously changing the cybersecurity game. The Cost of Insider Risks Global Report validates this, with more than half of companies now using AI to detect and prevent insider threats.
What now? When it comes to insider risk management, analysts are the first line of defense. Companies that leverage AI tools and capabilities to support threat hunting are gaining a crucial advantage in expediting investigations, democratizing data analysis, and fast-tracking detection of insider risks, all while reducing the skill requirement (pg. 15 of the report).
Summing up
As insider risk management budgets expand, companies have a prime opportunity to make very dollar count in pursuit of breach prevention.
Now is the time to turn insights into action, to achieve a trusted and protected workforce underscored by protective security and resilience.
Topics
Subscribe today to stay informed and get regular updates from DTEX Systems