Earlier this year we published our 2023 Insider Risk Investigations Report and took care to ask the question, what are we solving for? Why? Because too often, we see the conversation focused on insider threat management as opposed to insider risk management. Focusing on insider threats, however, is reactive. After data loss occurs, the only real option for organizations and their risk teams is damage control. To genuinely prevent data loss, the conversation must focus on proactive insider risk management and getting ‘left of boom‘. This demonstrates the need to distinguish insider risk from insider threat.
Insider Risk
At the most basic level, anyone who handles data is an insider risk. This includes your Board and C-level executives all the way down to your newest and most junior employee. It also includes your partners, attorneys, and third-party suppliers. To be clear, it’s not that all these ‘insiders’ intend to cause harm. Insiders are risks because they are human, and humans make mistakes all the time. From losing devices to accidentally sending sensitive emails to the wrong recipients.
Sometimes, however, a ‘risky’ behavior isn’t an accident, but simply an attempt to work more efficiently. For example, an employee who finds a workaround to access or collaborate on files because existing corporate security controls are tedious or slow.
What’s important to note is that while every insider threat was once a risk, not all insider risks necessarily go on to become a threat. And given most data loss incidents originate from non-malicious insider risks, it makes sense to focus on insider risk management. In practice, this means understanding and identifying the different types of insider risks early in the Insider Threat Kill Chain, and enforcing resolution to stop those risks from becoming threats that eventuate into data loss incidents.
Insider Threat
Insider threats are a subset of those who handle your data, and are considered further along the Insider Threat Kill Chain (i.e. closer to exfiltration). Threats are characterized by their malicious intent. They’re the employees, vendors, or partners who plan and execute actions to steal or leak sensitive data or sabotage corporate systems.
MITRE Corporation offers the following framework for distinguishing between the different types of insiders:
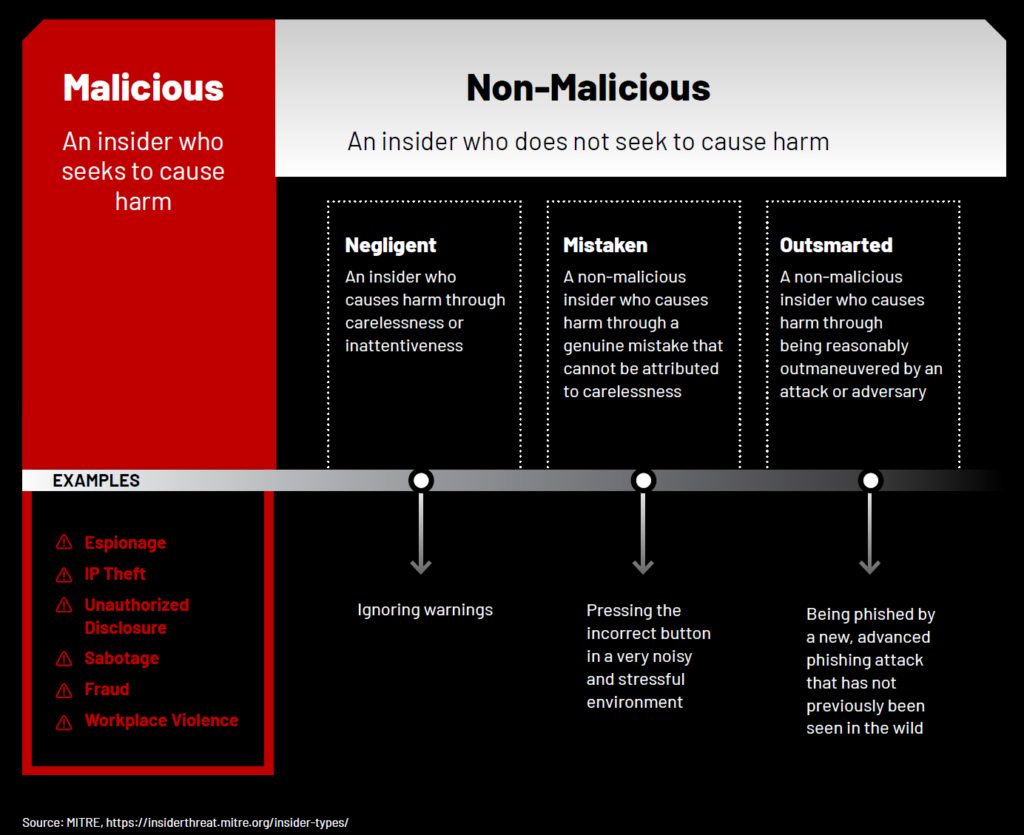
Make no mistake — your internal data has value. An employee planning to jump ship and take a role with your top competitor may be tempted to take your customer list or product plans with them. Others may be approached by external actors offering to compensate them financially in exchange for their help exfiltrating data. In rare cases, insider threats can be those individuals using corporate assets to engage in criminal behaviors such as black-market e-commerce, human trafficking, or child pornography collection and storage.
Our 2023 Insider Risk Investigations Report dives into the behaviors of both insider risks and insider threats.
To learn about the difference between insider risks and insider threats, and the specific behavioral risk indicators, download our 2023 Insider Risk and Investigations Report.
Subscribe today to stay informed and get regular updates from Genesis Global






