Earlier this month the Department of Health and Human Services’ Health Sector Cybersecurity Coordination Center (HC3) issued a report on the risk to the healthcare sector from malicious insiders. Why now? The Lapsus$ group hack of Okta and subsequent breaches at healthcare organizations brought to light the risk to all organizations from malicious insiders.
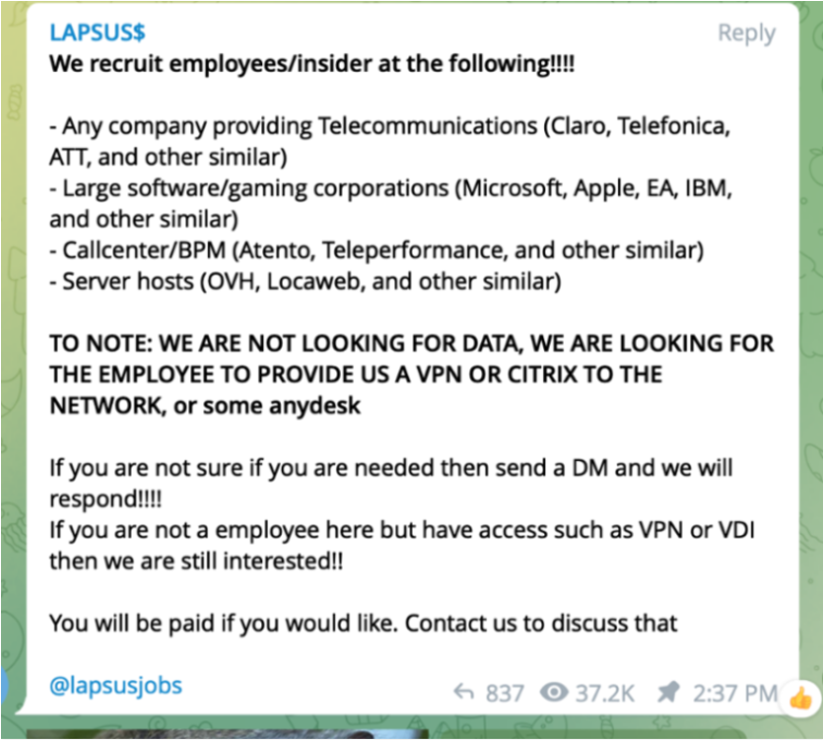
The HC3 brief defined an insider threat as, “a person within a healthcare organization, or a contractor, who has access to assets or inside information concerning the organization’s security practices, data, and computer systems.” This aligns with tactics used by Lapsus$. Rather than relying on sophisticated attacks, Lapsus$ recruited disgruntled employees using Telegram. Instead of stealing data directly, Lapsus$ requested guidance and legitimate credentials to the internal network via a VPN or Citrix.
The HC3 brief calls out three specific risks in the healthcare setting:
• Fraud – Healthcare organizations collect personal health information (PHI) on patients that can be leveraged for insurance fraud
• Data theft – Credit card information can be sold on the dark web and personally identifiable information (PII) can enable identify theft
• System sabotage – Ransomware attacks can make it impossible to access patient records. In a separate advisory this month regarding the Hive ransomware group, HC3 recommended that healthcare organizations, “be aware of their operations and apply appropriate cybersecurity principles and practices.”
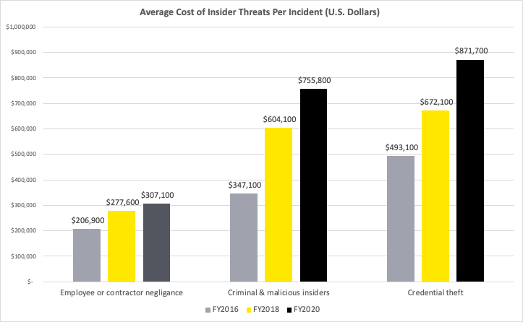
The costs from malicious intent is more than double those from negligence
The brief highlights the costs to organizations from malicious insiders and external threats (credential theft) are much higher than the costs from negligence. The average cost per incident from credential theft is 184% more than losses from negligence and malicious insider incidence are 146% more than costly.
How do you protect data when everyone can access it?
One study found that on average almost 20% of sensitive files are open to every employee in healthcare organizations. When everyone has access to the crown jewels, security cannot simply focus on those files. Instead, it requires organizations to understand actions taken with that data in context.
The HC3 brief mentions specific indicators of intent, including creating backdoor accounts, installing remote network administration tools, and accessing systems or machines of other employees. While these rule-based defenses are obvious, our research shows that a technically proficient internal or external threat can easily bypass these to steal data. Our research with MITRE shows that these threat actors can identify, collect, and exfiltrate data in ways that appear to be normal activity. They understand what these systems are watching for and simply avoid using those.
Recommendations
Malicious insiders and those posing as legitimate users present a constantly changing threat space. HC3 recommends the following:
- Revise and update cyber security policies and guidelines—What worked last year is not necessarily the best approach today.
- Limit privileged access and establish role-based access control—Healthcare organizations, like others handling sensitive information, should adopt least-privilege strategies.
- Implement the zero trust and MFA models—Zero Trust architectures turns on its head the notion of “trust someone forever who has logged in” and applies a model of “trust, but verify” to every interaction with a system.
- Back up data and deploy data loss prevention tools—Diligent back up policies can help organizations recover from ransomware attacks. We would caution teams, however, to avoid past mistakes of rigid policies and complex rules from DLP solutions that hamper user acceptance and productivity. Skilled insiders can also bypass these fixed rules. Instead, focusing on analyzing user actions in context can uncover indicators of malicious intent.
- Manage USB devices across the corporate network—Removable storage devices are a common exfiltration vector for malicious insiders. Limiting their use provides a layer of protection against malicious insiders with average skills.
The HC3 brief also provides high level guidance on detecting and responding to insider threats, including:
- User Activity Monitoring—User activity monitoring (UAM) solutions monitor and log all activity by users, including keystroke logging, screenshot captures, keyword monitoring, browser and search recording, and video recording of sessions. While helpful in forensics and when a threat is clearly identified, UAM’s surveillance capabilities can be used in a way that is disproportional to risk. Organizations must also use UAM carefully to comply with privacy regulations like the EU’s General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA). All forms of data collection are subject to these regulations and organizations must access, use, and protect the data properly.
- Logging and auditing—Security Information and Event Management (SIEM) solutions collect log files from devices to identify anomalous user behavior. This also is essential in forensic analysis.
- Incident detection and response—Insider threats follow a “kill chain” of reconnaissance, weaponization, delivery, exploitation, installation, command and control, and actions of objectives. An attack can be successfully stopped at any point in the kill chain.
- User and Entity Behavior Analytics (UEBA)—UEBA solutions analyze large datasets to model typical behaviors of people and machines—a baseline— within a network. Once a baseline is established, anomalous activity indicative of a threat can be identified. UEBA often use machine learning to improve performance over time.
- Employee Education—Organizations that help their employees understand how data can be put at risk will fare better. Training on general security awareness can help thwart phishing attacks and fraud. Personalizing security through education on identity theft and the importance of an organization’s reputation can help build an improved security culture.
The HC3 brief has many more tips. You can read the guidance here. To learn more about how DTEX Systems helps organizations address these threats, download our 2022 Insider Risk Report.
Subscribe today to stay informed and get regular updates from DTEX Systems





