Insider threat is a security issue that’s constantly floating in limbo. It’s significant enough to net some discussion, sure. But for a lot of organizations, it just isn’t a pressing priority.
That is, it isn’t until an enterprise experiences an incident themselves. Then it becomes top-of-mind for the next couple of months. Sometimes, these incidents trigger major security changes. But too often, it just fades back into the background.
As we say around the Dtex offices: every year, insider threat is #5 on every CISO’s top five priorities for the year. And the budget line is drawn after #3.
But on some level, this is understandable. Often, the insider threat can feel like an intangible concept. It’s difficult to identify or quantify the insider threats within a particular organization. Plus, there an even bigger problem: most enterprises aren’t aware of how much an insider threat attack can cost, because that information just hasn’t been available.
Well, we decided that it was about time to change that.
Introducing the 2016 Cost of Insider Threats Report
It’s time to find out, once and for all, the financial impact of insider attacks. Today, we released the 2016 Cost of Insider Threats Report.
We teamed up with the Ponemon Institute to pin down the real numbers. When it comes to security and technology research, Ponemon is well known. They’ve got a lot of experience in calculating the true costs of security risks.
Ponemon talked to 240 IT and security practitioners about insider threat. These were spread out across enterprises of all sizes and from all types of industries.
We always knew that insider threats were costly. But it’s been a huge eye-opener to see it laid out in such clear terms.
The Three Types of Insider Threats
Before we dive into the results, it’s important to note how we defined an insider threat. Some security professionals have a very narrow or vague view of what they consider to be an insider threat. But in our experience, insider threats fall into three main categories.
The Malicious Insider
When most people think of the insider threat, this is what they imagine. This is the disgruntled employee who sabotages company data as revenge. This is the law firm partner who steals proprietary data to take to their new firm. This is the customer service rep who copies credit card data to sell online. This is Snowden. You get the gist, right? This is anyone who intentionally harms their employer, whether that be for revenge, personal gain, or any other reason. They know exactly what they’re doing.
The Negligent Insider
Here’s one that a lot of people don’t consider — but they should (and you’ll see why shortly). These are well-intentioned employees or other users who accidentally harm the enterprise. We”ve written before about why it’s such a huge issue. Frankly, these incidents happen all the time. Employees constantly make mistakes that put company data at risk — whether that be because they’re careless, taking shortcuts, or simply uneducated in security. These sorts of mistakes lead to some of the biggest CISO headaches around. Ransomware, for example, is often put on a computer because of an employee’s careless browsing/download habits. Phishing attacks are another great example.
The Credential Thief
These are outside hackers who steal credentials to gain inside access to your system. A lot of people don’t put these guys under the umbrella of “insider threats.” But we’ve always thought that’s where they belong. Here’s why: once an outside gains access to your system, they are effectively acting as an insider. The methods that you need to detect and stop them are the same as any other rogue employee. They’re a danger operating from within your environment, so they are very much an insider threat.
Incident frequency by insider type
The surveyed organizations experienced a total of 874 insider incidents over the past year. 598 of those were negligent insiders. 191 were malicious insiders. 85 were credential thieves.
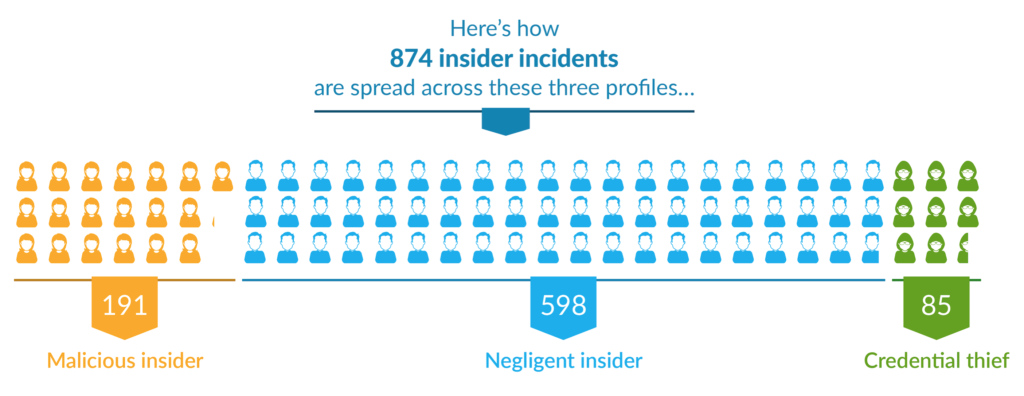
We probably don’t even need to point out that negligent insider incidents vastly outnumbered malicious insiders and credential thieves, do we? That much speaks for itself. But what does that mean for organizations? Does it actually translate to a substantial cost risk? Well…
Show me the money!
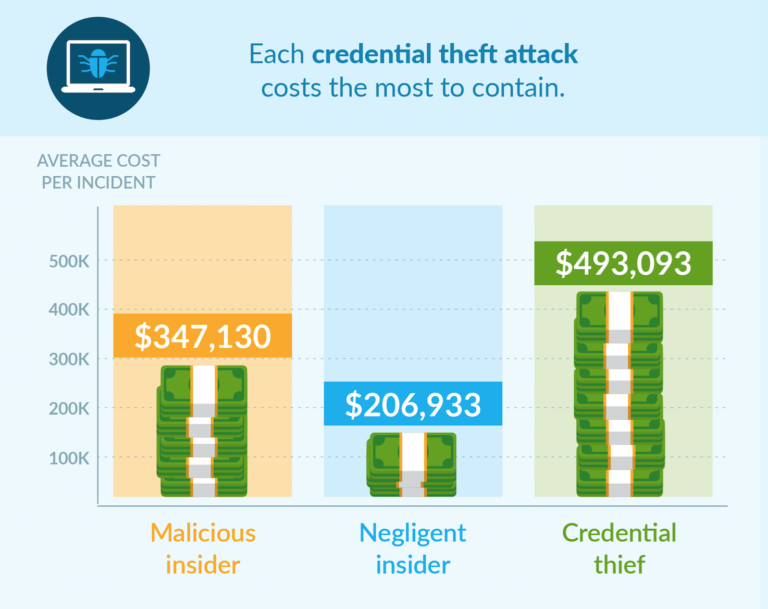
As you might suspect, each of these types of insider attacks has a different containment/remediation cost.
An attack from a malicious insider costs an average total of $347,130. Meanwhile, a negligent insider incident costs $206,933. And finally, a credential theft incident costs $493,093.
So that means that negligent insider attacks are the least costly and infiltrators are the most costly, right?
It’s not that simple.
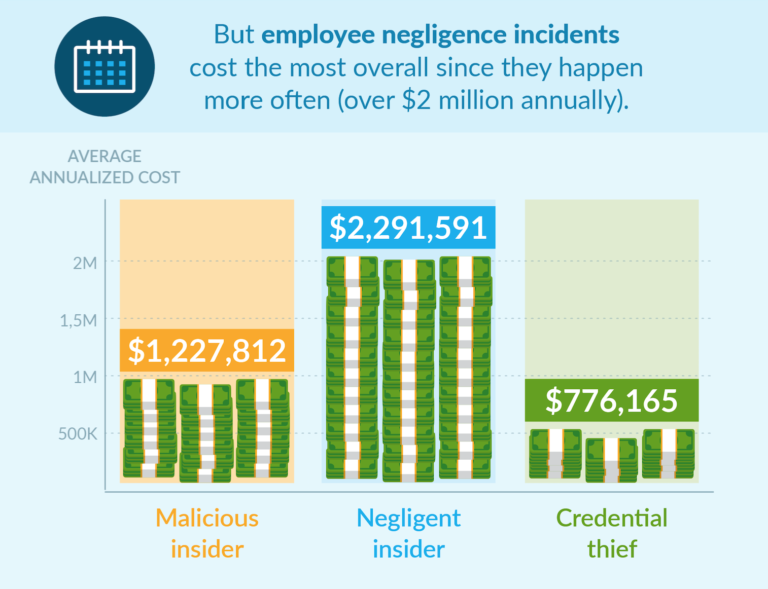
When we look at the total annual cost by incident type, we get a whole different story:
The average total annual costs of negligent insider incidents add up to $2,291,591 — by far the highest of the three. But it’s not like malicious insider incidents or credential thefts are cheap, either. They cash out at $1,227,812 and $776,165, respectively.
So you’re saying insider threat incidents cost organizations millions of dollars?
In a word, yes.
And here’s the real kicker: when you take all three of these types of attacks into consideration, the total is staggering.
The average total annual cost of containment/remediation for all types of insider threat is $4,295,568.
That’s a lot!
Response time makes a difference.
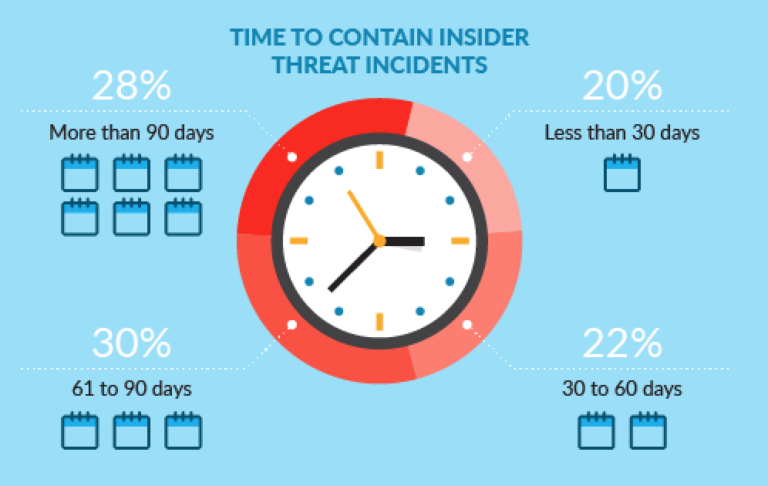
We also noticed another critical factor in costs: remediation time.
The organizations that Ponemon surveyed were fairly evenly split when it came to containment times. 20% took less than 30 days to contain an incident, 22% took 30-60 days, 30% took 61-90 days, and 28% took more than 90 days.
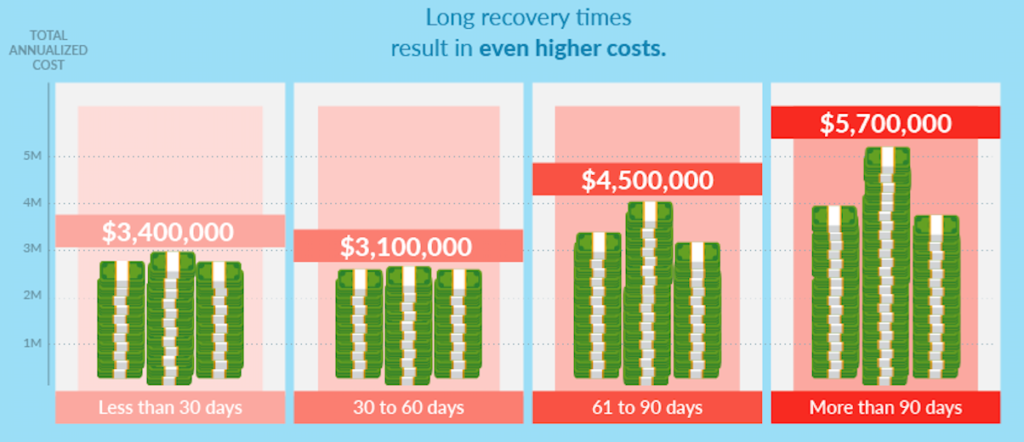
As you might be able to guess, longer recovery times meant higher annualized costs. Organizations who could contain an incident in under 60 days had average annual costs from $3,100,000 – $3,400,000. But organizations that took 61-90 days had costs of $4,500,000. And if they took more than 90 days to contain incidents? Then their costs were sky-high: an average of $5,700,000.
This just confirms what a lot of people (including us) have been saying for years: response time matters. The quicker you can detect, find, and stop an insider incident, the less these incidents will cost you. That’s why visibility and the ability to pinpoint real risky activity are so important!
I get it, insider threats are expensive! Now what?
It’s time to start thinking about the solution.
There are dozens of companies out there who claim to solve the insider threat. It’s a crowded and confusing landscape — and it’s even worse because all of these vendors have very different kinds of solutions. How can they be so different and all claim to stop insider attacks? And more importantly, do they actually work?
Well, like most things in life, there’s no black-and-white answer. But we did discover something interesting in Ponemon’s data.
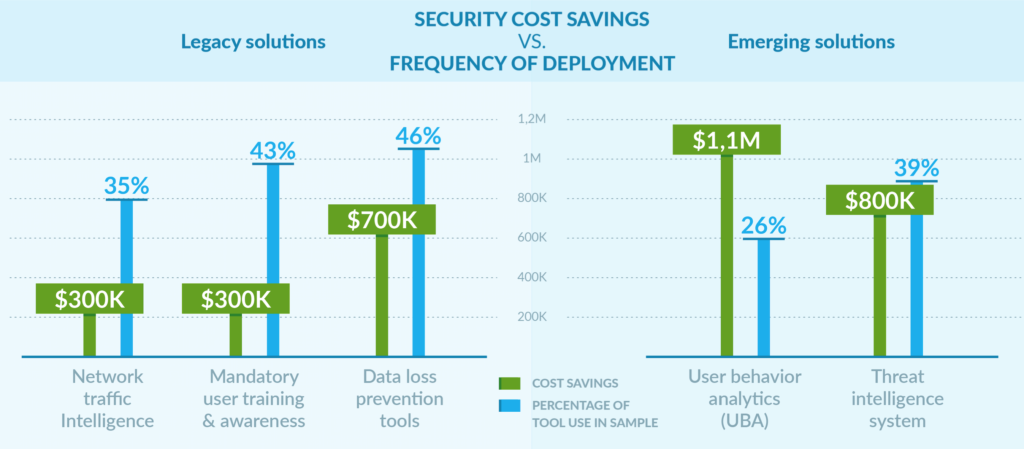
Legacy solutions were most commonly deployed at the surveyed enterprises. These are old-style solutions that tend to rely on inflexible blocking or heavy, out-of-date technology. But even though they were the most frequently deployed, they also showed the lowest impact in reducing risk.
On the other hand, we saw a different story with newer, emerging technologies. Most of these rely on intelligence and analytics over lock-and-block methods. They have a much lower adoption rate — but a much higher cost-saving potential.
The truth is, no single solution alone is going to be able to completely 100% stop all insider threat attacks. That’s a guarantee that no vendor can make.
But we can comfortably say that it’s more effective to use flexible, intelligent solutions that provide knowledge and visibility. Blocking is simply no longer manageable in today’s ultra-connected, ultra-portable world.
And of course, a layered defense is the best solution of all.
Ready to learn more?
This is just a partial overview of what we discovered in the 2016 Cost of Insider Threats report. To get the full report and see all of the findings, download the full PDF here.
Already looked at the report? Maybe you’re ready to begin building an insider threat program of your own? The first step is to see what’s really happening in your organization. An internal risk assessment can show you exactly what your current security system is missing.
Interested in learning more?
Subscribe today to stay informed and get regular updates from DTEX