Act now to mitigate risk:
- Insider risk monitoring program.
- Server monitoring for abnormal user behavior.
- Encryption, patches and secure edge devices.
- Relevant employee training.
Some parts of this Threat Advisory are classified as “limited distribution” and are accessible only to approved insider risk practitioners. To view the redacted information, please log in to the customer portal or contact the contact the i³ team.
INTRODUCTION
The “Salt Typhoon” and “Volt Typhoon” cyber espionage campaigns starkly revealed vulnerabilities in critical infrastructure and the growing danger of insider threats and compromised supply chains. These breaches exposed sensitive data and disrupted operations, underscoring the urgent need for robust internal security and vigilant supply chain monitoring.
This Insider Threat Advisory (iTA) provides a review of the current reporting surrounding Salt Typhoon and Volt Typhoon and their behaviors and indicators from an insider risk perspective. There is guidance and advice from multinational intelligence agencies on Joint Guidance: Identifying and Mitigating Living Off the Land Techniques which nation state actors like those in the Typhoon groups utilize.
Recent reports on Salt Typhoon and Volt Typhoon indicate that they are targeting vulnerable edge devices, bypassing phishing emails and MFA fatigue attacks by directly compromising these devices. Their strategy often involves targeting known vulnerabilities, particularly in organizations with slow patch management processes.
EARLY DETECTION AND MITIGATION
Server monitoring for abnormal user behavior
Monitoring servers for abnormal user activity is crucial, especially in environments where users typically have admin access and activity levels are generally low. Admin accounts have elevated privileges, making them prime targets for malicious actors. Unusual activity, such as unexpected login times, access to sensitive files, or changes in system configurations, can indicate potential security breaches or insider threats. By keeping a close watch on these activities, organizations can quickly identify and respond to suspicious behavior, thereby protecting critical data and maintaining the integrity of their systems.
Within our DTEX InTERCEPT detect and investigate section there are many server-specific actions that can be reviewed or monitored. For organizations that are likely targets of nation state actors like this (such as critical infrastructure) there may be organization specific behaviors and indicators that could be added to the existing rule-base to enable faster detection of malicious behavior.
Insider risk monitoring program
Having an insider risk management program is crucial for organizations to protect against insider threats that can lead to significant security breaches. Such programs help identify and mitigate risks posed by employees, contractors, or partners that have access to sensitive information. By monitoring user behavior, integrating HR data, and tracking credential usage, organizations can detect anomalies and prevent data leaks, financial losses, and reputational damage. An effective insider risk management program not only safeguards critical assets but also fosters a culture of security awareness and accountability among employees, ultimately enhancing the overall resilience of the organization.
- Employee work groups: These offer a comparative behavioral baseline, flagging deviations from established patterns. When enabled within a monitoring tool, they enhance detections by allowing comparisons against group norms, helping to identify deviations from typical job responsibilities.
- Hours of work: Monitoring hours of work can be complex for global organizations. A forensic audit trail helps track user behavior over time and flag unusual situations, such as a user account appearing on an unexpected device, which may indicate suspicious activity.
- HR integrations: Integrating HR data provides crucial context, such as employee leave or role changes. Combined with hours of work and location data, this information helps identify anomalies related to employee availability and access patterns.
- Credential storage access monitoring: Monitoring how and where credentials are stored is critical for early detection of potential compromises. Organizations should implement mitigations to prevent employees from saving work credentials in personal accounts. Tools like DTEX InTERCEPT can use HTTP Inspection Filtering to detect and monitor instances where credentials are saved in browsers or other applications, helping to identify risky behavior before it leads to a compromise.
By leveraging these features, organizations can create a comprehensive insider risk detection strategy, enhancing their ability to identify and respond to potential security issues effectively.
Encryption, patches and secure edge devices
Ensuring a secure system and its components is vital for mitigating risks in the telecom industry. Telecom companies must implement robust encryption protocols to safeguard data transmitted across their networks, preventing unauthorized access and data breaches.
Regularly updating software is crucial to patch vulnerabilities that hackers could exploit. Monitoring user activity helps detect suspicious behavior early, allowing for swift intervention. Conducting regular vulnerability scans identifies potential weaknesses in the system, enabling proactive measures to address them. This can include third-party or open-source software, like Python packages. In a 2022 example, PyTorch’s code was compromised when an attacker put a package on the same name in the PyPI index which got precedence to be installed. This is a similar to what is seen in DLL preloading attacks.
Maintaining up-to-date edge devices is essential for blocking unauthorized access and protecting the network from external threats. By integrating these protective measures, telecom companies can create a resilient security framework that minimizes risks and ensures the integrity and confidentiality of their services.
Relevant employee training
Employee training is essential for preventing and detecting insider threats. By educating employees on security best practices, companies can reduce the risk of accidental data breaches and ensure that staff are aware of potential threats.
Training programs should cover topics such as recognizing phishing attempts, proper data handling procedures, and the importance of reporting suspicious activities. Additionally, fostering a culture of security awareness encourages employees to take an active role in protecting sensitive information.
Well-informed employees are better equipped to identify and respond to insider threats, ultimately strengthening the organization’s overall security posture.
DTEX InTERCEPT: DETECT AND INVESTIGATE
The are a significant number of articles around discussing Salt Typhoon and Volt Typhoon however there are virtually none that detail an internal investigation report for an end-to-end attack. The closest and most detailed is this Joint Cybersecurity Advisory from June 2023, which details some of the stages of the cyber kill chain that have detailed commands to use as atomic indicators. Within this section we will use these to threat hunt and build rules but also review other articles and behaviors to build a profile in order to strengthen early detection of nation state actors.
Initial foothold onto edge devices and servers
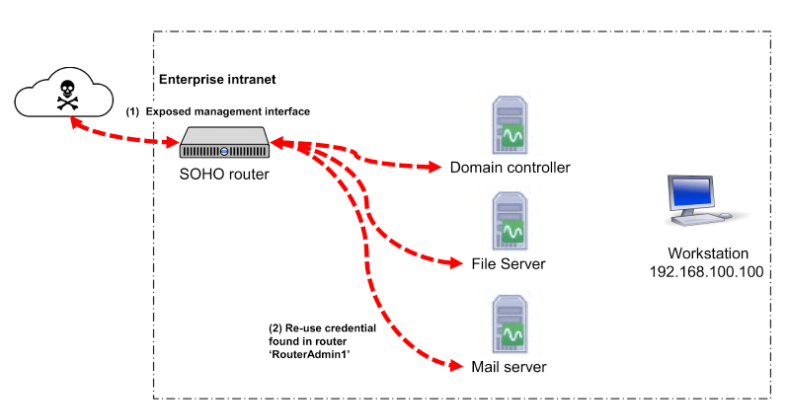
Based on our reading the initial foothold gained by these Chinese-based state-backed attackers is through actively exploiting vulnerabilities in edge devices either through unpatched CVEs or the less likely zero-days, even though a Microsoft blog indicates that Volt Typhoon has used an unknown Fortinet exploit.
Best practices recommend separating administrative and standard user accounts for enhanced security. This aligns with the principle of separation of duties; for example, an edge device administrator account should not possess domain administrator privileges. Implementing these mitigation strategies minimizes the impact of a credential compromise, even if an attacker bypasses multi-factor authentication (MFA).
Next, monitor these accounts for unusual activity beyond their typical usage patterns. This includes unusual login times, initial logins from unfamiliar devices, logins from locations inconsistent with the account’s profile, and suspicious command-line activity.
Abnormal hours of use
In iTA-24-08 i3 Threat Advisory: Printing Secrets, we covered an example of reviewing a single users activity profile. This is an example for Insider Risk Practitioners to get data on how an account may be used. For server administrator accounts this may be fairly sporadic but still fit within a “workday”. Obviously if multiple people are using a shared account this reduces its effectiveness and also goes against best practice.
Bonus: Unusual location of login
Even when attackers use VPNs, this approach can be effective because their IP addresses likely differ from those of authorized administrators. For remote access, server administrators should be added by on-site personnel, their IP addresses (either static or from their known ISP) whitelisted, and access time limited.
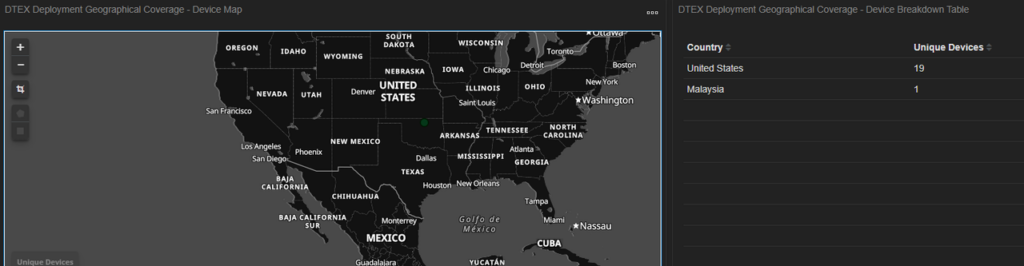
First logon to new endpoints
Based on the Microsoft blog we know that Volt Typhoon:
“… attempts to leverage any privileges afforded by the Fortinet device, extracts credentials to an Active Directory account used by the device, and then attempts to authenticate to other devices on the network with those credentials.”
This could either be through using the Active Directory account directly or applying the privileges to the account they currently have access to via impersonation. In any case, if separation of accounts and segregation of duties is applied within the organization’s environment then it should be easy to detect when there is a first logon event from a user account to a new endpoint. Within this Cloud Security Alliance writeup they provide the likely scenario that the threat actors would move laterally from the edge device into one of the servers, as illustrated in their image below:
In addition, the user would also be identified in the Leavers and Joiners dashboard as outlined in iTA-24-07 i3 Threat Advisory: Inside the DPRK: Spotting Malicious Remote IT Applicants.

Logins to endpoints outside their account description
Organizations may lack the initial logon event because a Domain Administrator account was used to configure their file servers. Even if this account hasn’t logged in recently, it doesn’t generate a first logon event.
Suspicious command line activity
Furthermore, behavior monitoring is crucial, requiring close collaboration between the insider risk team and IT to understand expected server administration behaviors and tool usage. Enhanced collaboration helps address the complex challenges posed by elevated privileges, shared tools, the use of living-off-the-land techniques by Chinese-based threat actors, and the diverse tasks and environments faced by individual administrators.
SUPPLY CHAIN COMPROMISE EXAMPLE: PYTORCH
We mentioned earlier that PyTorch had a security advisory where one of their nightly package updates was hijacked and malicious code added. This technique could be used to upload malicious code during a routine system update, or threat actors could exploit a supply chain attack to compromise an organization and then conduct a seemingly legitimate update. Monitoring and reviewing these activities, in conjunction with previous threat detections, could significantly aid in identifying malicious attacks.
Credential access
Domain controllers and some Linux servers often store credentials directly on the endpoint, making them prime targets for attacks aimed at harvesting account credentials and maintaining persistent access.
Windows Domain Controllers have a file called the ntds.dit file. This file contains Active Directory information, including user account file hashes. Because it’s a likely target for attackers, they may attempt to copy it for offline analysis (access is impossible while the server is online) and exfiltration for subsequent brute-force attacks against the hashes. If the attackers are utilizing PowerShell and the required Windows event logging is enabled as described below in the section “Threat actor uses PowerShell to enumerate event logs or other commands” then the following queries could be run.
Linux servers locally store credentials split across two files: one is the passwd file and the other is the shadow file. If an attacker were to exfiltrate both of these files, then they could apply brute force password cracking methods to extract the credentials saved within. There are many methods to extract these files with administrator privileges, e.g. an attacker could use the cat command to make a copy of the contents into a file called test1.
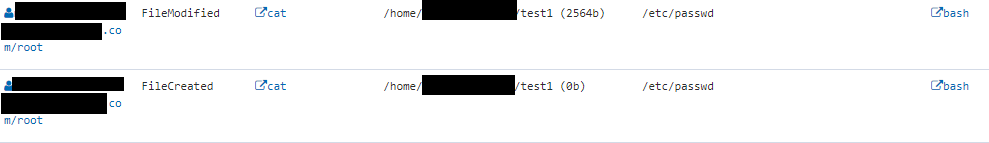
Use of common directories to store stages of exploitation
Cyber attackers often take advantage of easily accessible folders, such as those mentioned below, as they generally provide all users with read and write permissions by default. Depending on the system’s configuration, these folders may serve as accessible network shares, offering attackers established access points.
Example:
C:\Windows\Temp C:\Users\Public C:\Users\Public\Appfile C:\PerflogsThreat actor uses PowerShell to enumerate event logs or other commands
Example:
Get-EventLog security -instanceid 4624 cmd.exe /C "wmic path win32_logicaldisk get caption,filesystem,freespace,size,volumename" "cmd.exe /c "netsh interface portproxy add v4tov4 listenaddress=0.0.0.0 listenport=9999 connectaddress=<rfc1918 internal ip address> connectport=8443 protocol=tcp""Organizations must enable Windows Event Logs, ensuring the correct logs are selected for data capture. This would then generate the Activity_Group: WindowsEventLogActivity. Then insider risk practitioners could query and alert on the Microsoft-Windows-/Operational log for Event ID 4104. Note that these logs may not be enabled by default.
Filenames for previously known malware, scripts and tools
Example:
| backup.bat | cl64.exe | update.bat | Win.exe |
| billagent.exe | nc.exe | update.exe | WmiPrvSE.exe |
| billaudit.exe | rar.exe | vm3dservice.exe | WmiPreSV.exe |
| cisco_up.exe | SMSvcService.exe | watchdogd.exe |
Usage of PSEXEC
This could be a tricky one depending on whether or not psexec.exe is used extensively within the server environment. If the commands are issued through PowerShell with script block logging enabled, then insider risk practitioners may be able to determine the actions taken. If not, then alerting on the use of the executable could be valuable in tracking valid accounts which now be controlled by malicious threat actors.
PSEXEC example remote command execution:
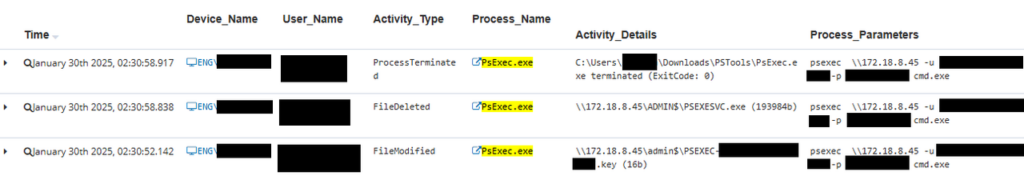
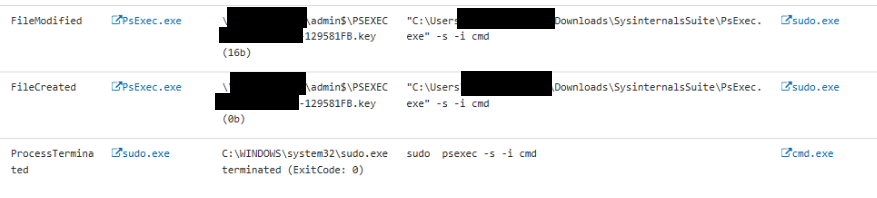
Regularly monitoring endpoints, particularly servers, for the presence of Microsoft Sysinternals tools is advisable. Although server administrators may sometimes need these tools, their ongoing presence on endpoints can create a security risk, potentially enabling nation-state actors to take advantage of them.
CONCLUSION
Insider threat detection necessitates collaboration with various teams and tools that monitor the organization’s environment. Nation-state adversaries, especially those with connections to China, are well-known for their stealthy tactics. Although their “living-off-the-land” techniques and minimal interaction levels are discreet, they remain identifiable. A comprehensive understanding of your organization’s current security landscape greatly enhances the probability of early detection of such malicious activities.
INVESTIGATIONS SUPPORT
Some parts of this Threat Advisory are classified as “limited distribution” and are accessible only to approved insider risk practitioners. To view the redacted information, please log in to the customer portal or contact the contact the i³ team.
RESOURCES
Identifying and Mitigating Living Off the Land Techniques | CISA
Joint Guidance: Identifying and Mitigating Living Off the Land Techniques






